In the previous post, we covered advanced ways to hack HID cards, so here we want to show ways to clone or copy a card in a day-to-day kind of environment with standard proximity (prox) cards which are based on 125khz . There are cloning services out there (like Clone my Key) who charge $20 per RFID / Prox card clone. Plus you need to send it in and wait for it. At the same time you might be able to buy a clone machine off of ebay or Amazon (read below) which is faster and cheaper.
Types of ID Card Hacks #
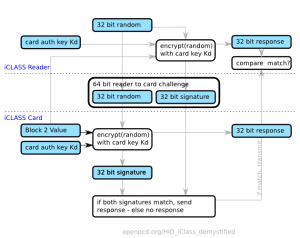
To be upfront: You won’t be able to clone any card like this. There are different card formats and depending on the type (see e.g. prox card hack from 2004 (!), long range card hack, iclass or wiegand hacks) you might need different- and more advanced methods. The differences lay in the depth of encryption, e.g. in the picture below we have an iClass encryption which shows the challenge - response from an iClass card and iClass reader - and here how it’s hacked. Read more about different types of HID cards here.
Easy, fast way to copy or clone your ID card #
The lowest cost, easiest way to quickly copy a simple keycard is to just get one of the RFID card ID copier (also called RFID 125Khz EM4100 ID Card Copier) from Amazon ($27 with free shipping) or eBay ($10.99 with free shipping).
Here are the instructions: “Easy to use : 1. Push the read button to read the card. 2. Take a new card and write on it. Very easy and comvenient :)” see it in action here:
Advance ways to build a key copy machine #
If you are ready for more advanced prox cards, here is a schematic for a reader / writer of RFID prox cards pdf to download which as 4 main components:
1) The clocking circuit, which generates a 4 Mhz clock for the microcontroller and a 125Khz carrier signal for the RFID interface.
2) The RF front end consisting of a tuned LC resonator and an AM peak detector
3) A series of low pass and band pass filters to extract the 12.5Khz and 15.6Khz FSK signals.
4) The SX28 microcontroller which performs the following functions: LCD initialization, Decoding and storage of the FSK data from the op amp filter output. Parsing and formatting of the card data. Driving the LCD display. Programming the clone card by modulating the 125 Khz carrier (per the T55x7 datasheet).
Be aware: This is really only applicable for simple prox RFID cards. It will not work for more advanced cards where we’d need to build a better keycard copy machine. If you’d like to better understand RFID System Design, download the pdf guide here.
Here are some more advanced links: #
From Kisi
- How to Copy RFID and NFC Access Cards & Key Fobs
- Any HID Keycard Can Easily Be Hacked Using A $10 device
- How HID Readers Are Hacked Using Wiegand Protocol Vulnerability
RFID Vendor Information
Videos
BlackHat Proximity Card Cloning Demonstration
RFID Hacking Demo - Sacramento Capitol Building
RFID Projects/Forums