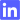Why do Businesses use Data Centers? #
For many companies, the data center is the heart and soul of their operations. Data centers support a number of core enterprise activities such as communication and file sharing, processing large datasets, and housing computing resources such as productivity applications, storage, and network infrastructure. To perform their various functions, data centers require robust computing hardware and powerful networking equipment. This is what allows them to aid companies and universities in processing large datasets for research, or allows for seamless collaboration amongst media professionals when working with large digital assets. Therefore data center security is paramount to an organization’s operations, productivity, and reputation.
Data Center Security: Introduction #
From an administrative perspective, there are a number of identity and access management (IAM) solutions available to organizations to ensure sensitive company data is secure and access to that data is properly restricted. However, given the large financial investment companies make on the physical components needed to build a proper data center (i.e. routers, servers, storage, and other associated hardware), data center physical security also plays a crucial role in hardware maintenance, as well as in preventing unauthorized physical access to equipment and data.
Integrating IAM with Data Centers Security #
From an IT perspective, data centers can be something of a double-edged sword. On the one hand, they centralize crucial company data, applications, and communication, making it easier than ever for employees to remain productive on the road via laptops, mobile devices, or remote workstations. However, this also means that sensitive company data is more at risk. The firewalls and intrusion prevention systems protecting company data at the data center have limited effects for remote workers who bring company devices outside the traditional network perimeter. Therefore, a more streamlined approach to authentication and authorization is needed to manage efficient access to data center resources. IAM solutions aim to be that consolidated approach, while also allowing for additional security measures such as single sign-on (SSO) and two-factor authentication (2FA).
There are a number of IAM software solutions available, such as Forefront Identity Manager, Microsoft Azure, and Okta Identity Management. It’s important to keep in mind, however, that the IAM software solution you choose must be able to:
- support your existing applications, servers, and databases
- be scalable to adapt to a growing volume of users
- be easily manageable for both a normal user and IT professional to help prevent disruptions in access and workflow.
For further streamlining and better ease of use, Kisi’s access control systems and products are compatible with a number of IAM software solutions.
Data Center Physical Security Checklist #
Now that we've covered how to set up the security infrastructure on an IT-level, let's dive into how to physically protect your data center room.
Here's a small checklist we've created:
- Carefully select the location where you plan to build the data center so as to mitigate the risk of damage from natural disasters or heavily trafficked areas.
- If you are physically building the room, select building materials with security and protection in mind (i.e. thick concrete walls, limited amounts of windows).
- Limit the number of entry points and have surveillance in place to carefully monitor who enters the facility and when. A solution for this would be to choose CCTV cameras, ideally paired with an access control system.
- This brings us to the next point that is: secure your data center with a proper access control system. Access control is crucial for data center security and every data center in the country has some access control measures in place. We will cover this point more thoroughly in the next paragraphs.
- Implement multiple layers of security and ensure that anyone entering the facility be authenticated multiple times (i.e. 2FA, biometrics, access cards).
- Ensure that the data center has access to two sources of utilities, such as electricity and water, in the event of an outage or emergency.
- Ensure that the data center’s design and infrastructure adheres to data center physical security standards such as ANTSI/TIA-942
It will be important for your organization to create a data center physical security checklist to facilitate the design of your data center. This will not only give you a starting point to begin your design, but also ensure that the specifications of your build will help limit wear and tear on data center equipment. For instance, a typical server room security checklist should include:
- Specifications related to room size, ceiling height, and building material type
- Equipment specifications to ensure proper emergency monitoring, access to electricity, and proper grounding
- Cooling specifications detailing aisle configuration, plans for back-ups, and underfloor cooling systems specifications
- Electric systems specifications that outline back-up power systems, emergency shutdown procedures, and grounding systems
Access Control for Data Centers #
There are three macro-reasons why access control is the standard when it comes to securing data centers:
- Physical security
- Compatibility
- Compliance
Physical security is obviously guaranteed when choosing access control as nobody apart from selected members of the personnel can access the room in question. However, physical security could be guaranteed even without access control. What really makes AC the ultimate security measure is how physical security combines with the two points we will cover in the next paragraphs.
With regards to compatibility, using a cloud-based access control solution allows you to integrate your current IT stack with the physical components of your space—decentral credential storage in each cloud-connected reader ensures remote management and 24/7 health status monitoring. Cloud-based access control technology also integrates with intrusion alarms, 2FA and SSO. A normal intrusion detection system or a legacy access control system cannot guarantee a level of compatibility like a cloud-based access control system (more on the difference here).
The third and last point is about compliance. In order to get your data center completely secured, you need to follow certain protocols both for the implementation of the system (see checklist above) but also for legal compliance. In the unfortunate event of a breach into the data center, you need to be able to quickly see who were the people that entered the room last and when. Kisi allows you, for example, to export in a matter of minutes, the last thousands of events that occurred in your facility. But this is not all. You can even, by pairing your Kisi system with video surveillance cameras, get snapshots of events like a door being held or forced open.
These three advantages, working together, make cloud-based access control an unexchangeable resource for the security of your data center.
Why Should a Datacenter Be Concerned with Setting Up Its Security Measures? #
Most secure data centers require a special environment to operate, such as a data center room or otherwise defined perimeters to provide access only to authorized personnel. They are a high-risk environment using large-scale electricity powers and robust equipment. Since data centers are often educational, research, or commercial entities, their malfunctioning can threaten sensitive personal or expensive commercial data, jeopardize user privacy and harm vulnerable environments.
Datacenter with electronic access door and floor ventilation
Think of the data needs of medical institutions, financial services or university records. Due to their ability to be “data banks” for most businesses, these data centers are in need of much greater physical and administrative control with special access privileges.
That is why most secure data centers not only introduce measures to comply with regulatory body requirements but also develop data center security policies to specify legitimate business needs and describe the access control system in detail.
Failure to set appropriate measures can cause large restoration for the datacenter, require insurance claim compensations, produce lawsuit costs and fees; not to mention two sometimes irreparable values - business reputation and loss of authority.
Implementing a Data Center Physical Security Policy #
It’s important to ensure that your data center physical security solutions are supplemented with a thorough data center physical security policy. These policies ensure that those with access to sensitive company information and expensive server equipment follow a standard operating procedure meant to mitigate the risk of data breaches and hardware damage. While following the example of other organizations can help act as a starting point for your own data center physical security policy, your policy could include some of the following elements:
- Detailed descriptions of access levels that are reflected on your cloud-based access control dashboard, as well as procedures for escorted access and remote access
- Guidelines for entry points (i.e. rules on key card access, propping doors, tailgating, and logging entrances and exits)
- Guidelines for reporting exceptions and/or unauthorized access, as well as an outline of procedures to follow in the event of remote cybersecurity threats like phishing, social engineering, and hacking
- Detailed outlines for safety and cleanliness policies, as well as policies for data center equipment deliveries, pick-ups, maintenance, and repairs
Overall, data centers play a critical role in an organization’s operations and productivity, but they are also expensive investments that house expensive equipment, sensitive data, and crucial applications. While data center security is complex and multi-faceted, it’s crucial to ensure smooth and safe operations at your organization. Kisi offers a number of services to help support your company’s security measures while also streamlining and simplifying the process.