Welcome to our “Access Control 101” lesson. Learning the ins and outs of physical access control can be overwhelming. That doesn’t have to be the case. That’s why we’ll discuss trends, review the basics, explore core components, and provide practical use case scenarios for various solutions.
Topic 1: Access Control Trends in 2022
- The shift to hybrid work is making office usage more dynamic, driving spaces towards the future. Buildings are converted to smart buildings, while workplaces are becoming tech-enabled, bookable on-demand infrastructures.
- The move to mobile, cloud, and IoT drives budgets to enable the workforce with a modern, scalable, and user experience-focused stack.
- IT compliance starts to require access control to be part of the IT compliance environment. SSO, SAML, encryption standards, and permission policies, as well as the escalation of alerts and alarms through IT systems, are part of this imperative change.
- Workplace automation and remote management rise in importance because crucial security processes can not rely on manual management and need to be remotely controlled.
Physical Security Market by Industry
Topic 2: Access Control Overview
Simply put, access control systems connect people with the physical spaces around them. They do so by extending access for authorized entry and restricting access for unauthorized entry. Physical access control can take many forms, including manual (doorman, guard), mechanical (physical keys), electronic (cards, fobs), and physical (turnstiles, barriers). Deciding the appropriate method will vary depending on several factors, like cost (upfront and recurring), security requirements, and the solution’s features.
Topic 3: Credentials
Technological advancements have increased the number of ways a space can be accessed. Here we’ll explore the most common credential forms.
Physical Keys
Physical keys are an excellent example of mechanical access control. Even though they are one of the oldest access control methods, they are still widely used both commercially and residentially to secure spaces. Keys are often used in residential settings or to secure spaces that don’t require 24-hour monitoring.

Use cases | Security | Cost |
|---|---|---|
Limited | Low | Negligible |
|
|
|
Cards
Cards often are the first thing that pops into our minds when thinking of keyless access. In reality, they are just one of the keyless methods available to secure a space. Cards are typically the size of a credit card and are used in conjunction with an electronic access control solution to provide entry to authorized persons. The ability to print on their surface allows them to double as an ID badge. Want to learn more about keycard access systems? Click here.

Use Cases | Security | Cost |
|---|---|---|
Numerous | Medium | Negligible |
|
|
|
Fob
Similar to cards, fobs are small coin-size credentials that offer greater durability. Since fobs are intended to go on the user's keyring, they are less likely to be lost or stolen. Learn more about fob access systems here.

Use Cases | Security | Cost |
|---|---|---|
Numerous | Medium | Negligible |
|
|
|
Stickers
Stickers (also known as tags) have varied applications and uses. They can be used as a standalone credential when applied to a vehicle to operate garages and gates or as an additional credential when applied to a 3rd party-building access card or ID badge.

Use Cases | Security | Cost |
|---|---|---|
Limited | Medium | Negligible |
|
|
|
Biometric
Biometric credentials are an example of credentials that look at who the user is rather than what the user knows (pin number) or has (fobs, cards, keys). These credentials are difficult to duplicate or forge as they measure data points unique to each user. Common biometrics include facial recognition, fingerprint, iris, palm vein pattern, and heartbeat, to name a few.

Use Cases | Security | Cost |
|---|---|---|
Numerous | High | Time |
|
|
|
Keypad
Keypad credentials consist of a numerical code that is shared with users of the space. Organizations that do not want to maintain physical credentials or enroll the biometric data of their users prefer keypad credentials. Depending on the deployment, all users of the space may be given the same code or receive a unique user code.

Use Cases | Security | Cost |
|---|---|---|
Limited | Low | Non-existent |
|
|
|
Cloud
Cloud credentials, allow users to obtain access through internet-connected devices like mobile devices and computers. Access to a space can be remotely operated by an administrator or users that have been granted access.
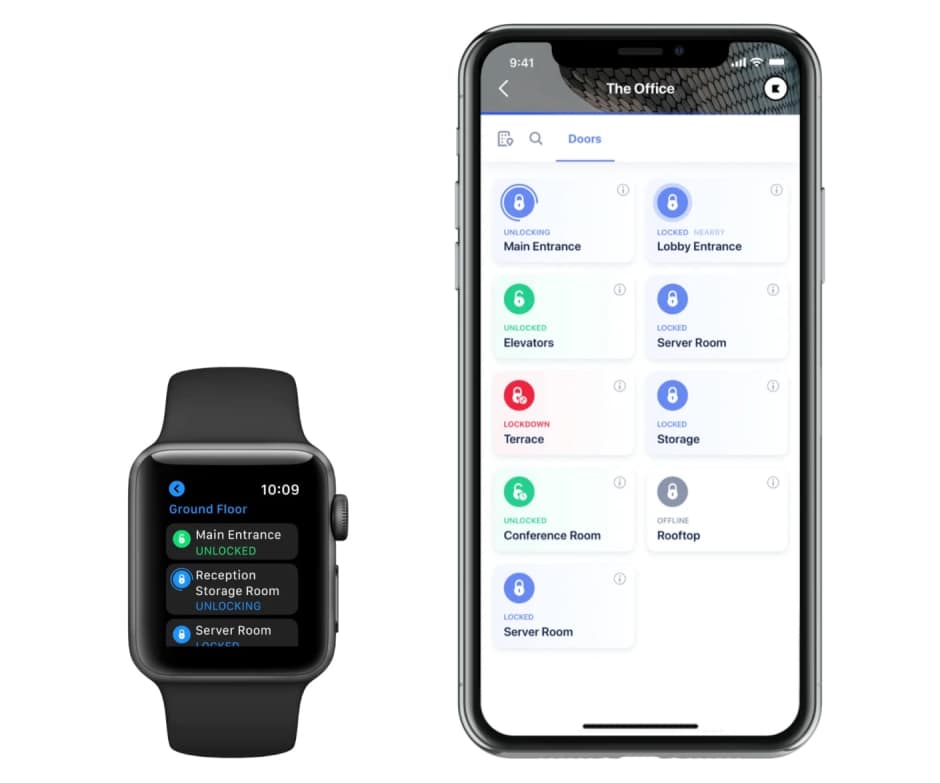
Use Cases | Security | Cost |
|---|---|---|
Numerous | Medium/High | Variable |
|
|
|
Mobile
Mobile devices, a relatively new credential form, have risen in popularity lately. This is mostly due to the enhanced security and convenience they offer. Mobile credentials typically rely on BLE (Bluetooth Low Energy), NFC (Near Field Communication), or an app-based credential to perform unlocks. The constant technological advancements are easily leveraged to prevent unauthorized access. For instance, before presenting their mobile credential to a reader, users might be required to first unlock their device using a passcode, facial recognition, or fingerprint.

Use Cases | Security | Cost |
|---|---|---|
Numerous | High | Variable |
|
|
|
Topic 4: Readers
Readers act as the gatekeepers for a space. When presented with credentials, they receive information about the user requesting access and confirm if the user is permitted to enter the space. So, let’s explore the capabilities, limitations, and considerations of the most common readers available.
Card Reader
Card readers require that a user provide a unique set of credentials to gain access to a space. Credentials may come in the form of a card, fob, sticker/token, or mobile device. When presented with credentials, to transmit the information, the reader will communicate with the credentials using technologies such as wireless, magnetic, Bluetooth, RFID and NFC. Authorized credentials will be granted access, while unauthorized credentials will be denied entry. You can learn more about how credentials and readers communicate here.

When determining the right card reader for your application, it is important to consider the following:
- Location: Does the mounting space have limitations with regard to reader size?
- Durability: Will the reader be placed indoors or outdoors? For outdoor readers: Is the reader able to withstand extreme temperatures? Is it waterproof?
- Cost: What is the cost of the reader hardware? What is the cost to install?
- Time: How long does new user enrollment take? How long does valid credential verification take?
- Security: Does the reader encrypt communications? Does the reader have any safeguards or protocols if it is tampered with? How many unique credentials are supported?
- Network: Is the reader able to connect to the network over ethernet or wifi? Will the reader work in the event of a network outage?
Biometric Reader
Biometric readers allow users to access an area by verifying something unique to the user, such as palm geometry, facial recognition, or iris scan. Biometric credentials are difficult to fake or forge since the credentials are highly unique to the user. Several readers on the market employ a form of liveness detection to ensure the credentials presented have not been spoofed. You can learn more about biometric access control here.

When determining the right biometric reader for your application, it is important to consider the following:
- Location: Is there ample wall or floor space to accommodate a biometric reader?
- Durability: Will the reader be installed outdoors? For outdoor readers: How is the reader protected from dirt and debris? Can the reader perform in extreme conditions?
- Cost: What is the cost of the reader hardware? What is the cost to install?
- Time: How long does new user enrollment take? How often will the reader need to be cleaned of dirt and debris? How long does valid credential verification take?
- Security: Does the reader employ a form of liveness detection? How are user credentials stored? How many unique users are allowed?
- Network: Is the reader able to connect to the network over ethernet or wifi? Will the reader work in the event of a network outage?
Keypad Reader
Keypad readers require that a user provide a valid PIN to gain access. Keypad readers don’t require that the PIN provided is unique to an individual user or that it even belongs to the user providing it. As long as the PIN provided is valid, access will be granted. You can learn more about keypad access control here.

When determining the right keypad reader for your application, it is important to consider the following:
- Location: Will the keypad be integrated with a door lock, or will it be mounted to the wall?
- Durability: Will the reader be installed outdoors? For outdoor readers: How is the reader protected from dirt and debris? Can the reader perform in extreme conditions?
- Cost: What is the cost of the reader hardware? What is the cost to install?
- Time: How long does new user enrollment take? How often will the reader need to be cleaned of dirt and debris?
- Security: Does the reader allow for random number generation, or are the keys static? How many unique PINs are allowed?
- Network: Is the reader able to connect to the network over ethernet or wifi? Will the reader work in the event of a network outage?
Multi-factor Readers
Multi-factor readers require that a user provide more than one credential form to gain access. This could include any combination of mechanical (keys), electronic (cards, fobs, mobile devices), biometric (fingerprint), or keypad (PIN) entry to validate a user's access. Readers that require more than one credential form increase the difficulty for an unauthorized person to fake multiple credential forms and gain access to secured spaces.

When determining the right multi-factor reader for your application, in addition to the previously mentioned considerations, it is also important to consider the following:
- Credential form: What combination of credentials will users be required to present?
- Time: How long does credential verification take? Can credentials be presented simultaneously, or does one credential need to be verified before the other credential can be verified?
Smart Locks
Smart locks refer to reader locks that also act as door controllers. These types of readers are most common in residential and hospitality applications. Mainly in settings with limited users requiring access or where integrations and analytics are unnecessary. Smart locks replace the existing manual lock door hardware with electronic access control locks. You can learn more about smart locks here.

When determining if smart locks are suitable for your application, it is important to consider the following:
- Cost: What is the cost of the smart lock hardware?
- Time: How long does installation take? How long does new user enrollment take?
- Security: How many users are supported? What communication methods are permitted?
- Network: In the event of a network outage, will the reader still work and perform unlocks?
Topic 5: Controllers
Controllers act as the brains for your access control solution. They are typically installed in secure places like the IT or communications room and connect wired electronic door locks to their relays. When a reader is presented with credentials, the reader will communicate the information from the credentials to the controller to verify the user can access the space. Once verified by the controller, the controller will then send a signal to the appropriate door relay to unlock.
In addition to performing unlocks for connected doors, most controllers are equipped to connect to fire alarm control panels, request to exit buttons, and door contact sensors.

Topic 6: Access Control Software
Choosing a software solution to tie your access control system together is arguably the most important component to consider when reviewing complete solutions. In access control, there are two primary methods for software deployment, cloud or on-premise. Here we’ll review the capabilities, limitations, and considerations of cloud-based and on-premise solutions.
Cloud
Cloud-based systems, sometimes referred to as Software as a Service (SaaS), are hosted on a remote, 3rd party server that is not owned by the organization deploying the solution. Cloud-based systems are attractive to organizations that do not have the people (IT staff), equipment (on-site servers), or facility resources (power and space) available to effectively deploy an on-premise solution.
When determining if a cloud-based solution is right for your application, it is important to consider the following:
- Deployment: Hardware is installed on-premise by an installer or the organization, and the software is accessible from any internet-connected browser. Updates, including enhancements or bug fixes, are pushed directly to production by the solution provider without downtime.
- Performance: The solution provider monitors the performance of their system, applications, and hardware. Understand how the provider communicates incidents and outages, and how many times they’ve had performance impacts over the past 6 to 12 months.
- Integrations: Does the solution support integrations with other systems already deployed (CRM, cameras, analytics, directories, etc.), or does the solution provide access to the API so custom integrations can be built?
- Accessibility: Cloud-based systems do not require an administrator to be on-site in order to access or make changes to the system. Any connected web browser will work.
- Security: Data security is the responsibility of the solution provider. Understand the providers' approach to security and how they handle hardware, transportation, cloud, and application security.
- Scalability: Adding additional hardware at geographically diverse locations, or even the same location will not require significant planning, internal resources, or servers. Since the service is subscription-based, the only consideration is a slight increase in the monthly fee.
- Cost: Cloud-based solutions eliminate the need for servers, power, space, and IT labor. Cloud-based solutions will have a monthly or annually recurring fee that is equitable to the resources consumed by the organization.
On-Premise
On-premise systems, as their name suggests, are on the premises where the access control solution is being deployed. They are hosted on an onsite server operated and maintained by the organization's IT team.

When determining if an on-premise solution is right for your application, it is important to consider the following:
- Deployment: Hardware is installed on-premise by an installer or the organization, and the software is installed by the organization’s in-house IT team. The time to initially deploy often takes longer than cloud deployment as the organization is responsible for setting up people and material resources in advance of the software installation.
- Performance: Updates, including software enhancements or bug fixes, are performed by the organization's IT team when necessary. The IT team is also responsible for overseeing server performance. Ensure the IT team has a sufficient budget available to upgrade servers and systems when necessitated.
- Integrations: These may be available from third-party camera or visitor management solution providers or they may require customization. Non-standard customizations may impact the speed at which an access control upgrade can be performed.
- Accessibility: On-premise systems only allow administrator access from an on-site network-connected computer. Since even minor changes to access control (removing a user's access or enrolling a new user) require the administrator to be physically on-site, the organization can’t make quick security or safety changes (initiate a lockdown) to their solution.
- Security: Data security oversight and performing regular data backups are the responsibility of the in-house IT team. It is important to ensure that your IT team has a qualified and experienced technician to protect your organization's data from cyberattacks while also remaining compliant with laws and regulations.
- Scalability: Scaling an on-premise solution requires the organization to allocate resources in the same way they did for the first installation. Understanding the additional costs associated with software licensing, server room resources, and IT resources are important. At some point, a dedicated IT resource may be required to oversee the performance and ongoing maintenance and security of the software and server room resources.
- Cost: The initial cost for an on-premise solution is much higher than a cloud-based system. Ongoing licensing, operational, and labor costs must also be accounted for in order to understand actual annual costs associated with the system.
Conclusion
As organizations embrace the hybrid work model, implementing a future-proof access control solution is crucial to facilitate remote system management. Before purchasing an access control solution, involve key stakeholders in the planning process to ensure the solution selected meets the current and future needs of the organization.
Planning considerations:
- Set a budget for upfront and recurring charges.
- If existing hardware is present, determine if it can be upgraded or if it will need replacing.
- Decide how users will access your space (credential form).
- Identify any integrations that will be deployed (directory, camera, CRM, etc.).
- Understand security and feature requirements of the IT team and administrator.
Save time. Enhance security.
Modernize your access control with remote management and useful integrations.
Continue learning


