Now that you’ve made the decision to install an access control system, you’re faced with the task of actually choosing one, configuring it, installing it, and onboarding your team. There are a lot of factors to consider here; it can certainly seem overwhelming, but Kisi is here to guide you through the process and make it as clear and easy as possible.
Important Factors to Consider Before Purchasing Access Control
Location
There are always two locations to install access control: At the door and in the IT room (communications closet). The first thing to consider is on which doors you actually want the access control system installed. In other words, you have to decide what doors, windows, or other access points you’d want secured in your office. Note - this is certainly not a decision that you need to take alone! For one, Kisi can connect you with a local installer who will visit your space and give you expert recommendations about how best to secure your space.
Overall, though, the objective is clear: you should seek to ensure the safety of your high-value assets, like servers, critical data, and generally all electronic equipment like computers or screens. In general, you’ll want access control at your front door or all points of ingress/egress to public areas, and also at entry points inside the office to sensitive areas like your server room. For more information about server room security check out our server room standards guide.
The controllers for the locks will be located in the IT- or server room and will have to be wired to the electronic door locks. When thinking about installation planning, the you’ll want to consider the possibility of running cables from your IT room to your door locks. The actual location of the controller is less important - with a cloud-based access control system you will be able to your doors centrally from your dashboard:
Screenshot of cloud-managed access control devices. You can monitor them from anywhere with an internet connection.
Type of Access Control
Beyond that, you’ll want to consider which type of system you’ll want to install. There are several options here - for more in depth coverage please refer to our Access Control Guide. If all you want is a simple physical lock with traditional keys, that’s rather straightforward - any installer worth their salt can quote you and install it in a flash. If, however, you want a more sophisticated, modern solution, that uses modern IoT hardware and can integrate with smart home/office systems, then you’ll want something similar to Kisi’s own solution.
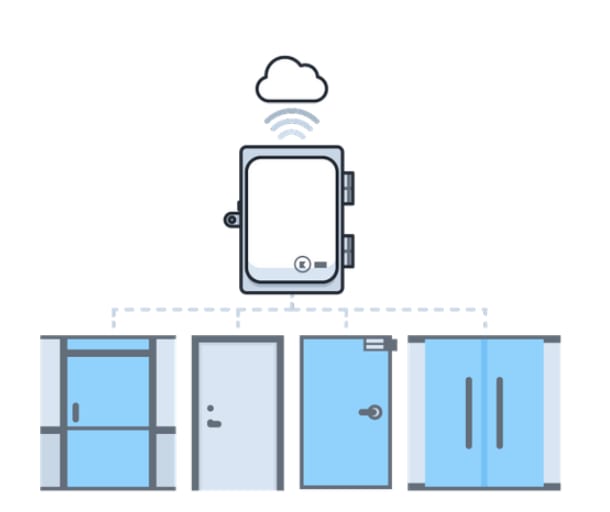
Cloud-based access control architecture (simplified)
Kisi, and most other leaders in access control, use cloud-based systems, meaning that at your office or space you will only have door readers and a cloud-connected controller, and all the data is handled by Kisi servers. This means that in the case of any malfunction or intentional tampering, your data will be secure, and Kisi can perform data analysis and help you glean insights into space usage. In addition, our modern readers are bluetooth and NFC enabled, meaning you can forget about having an extra card required for access: you can use your smartphone itself as an entry card.
Credential Types
This leads us nicely into the next factor to consider: credential- or authentication type. Different authentication types means different ways of authenticating (read: granting access to) a given user. The most basic form of authentication is the trusty old lock and key: a user/member is assigned a key to a lock for a door they are allowed access to, and then that key, when used, authenticates the user. Of course, there are many risks inherent with such authentication methods (not limited to key sharing or lost keys), so most modern companies opt for more modern authentication methods. These include, but are not limited to, keypads, key fobs, and NFC access cards, or even more cutting-edge systems like fingerprint or retinal scanners, and facial recognition cameras. If you have a system supporting different types of credentials you can typically select the credential type when sharing access:
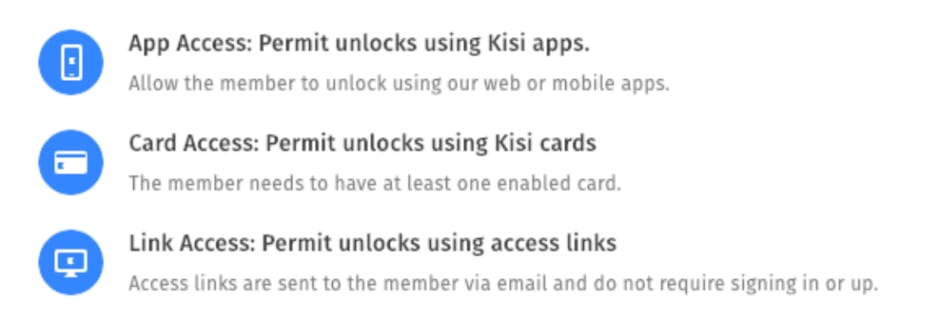
Selection in a modern access control system (Kisi) — allowing to choose between app, card or link access credentials.
Most access control companies fall somewhere in that range of authentication, with some like Kisi offering you the versatility of using legacy NFC cards or your own smartphone’s built-in NFC or Bluetooth capabilities (using your phone as a key card itself). Cloud-based systems use these methods as they allow for data communication back to the servers, which facilitates tracking and analysis.
Cost of Access Control
Last, but certainly not least, there is the cost of the access control system to consider. Often, though, with these systems, the hardware cost of the system itself is less significant when compared to the installation cost of the system and the locks themselves. There are many hidden costs with such a project, so it’s important to get in touch with a trusted salesperson or installer, and have some assurance that you are getting a fair quote for your needs. Furthermore, with cloud-based systems, there will often be a software licensing cost associated with the purchase. This is for data hosting on the servers and data analysis and tracking. While this might seem unnecessary, the service provided, and the fact that you will not need to purchase your own servers to host the data makes it very cost-effective. For a more detailed breakdown of the costs of physically installing access control, please consult this article on the Kisi blog.
Often, seeing a monthly or yearly license cost in the product is a sign of quality: The product will be hosted, maintained and supported on an ongoing basis, and the cost for that should be relatively transparent. Since even large companies including Microsoft, Google or Amazon move to those cloud based models, you shouldn’t get an access control needing a CD-ROM to get set up.
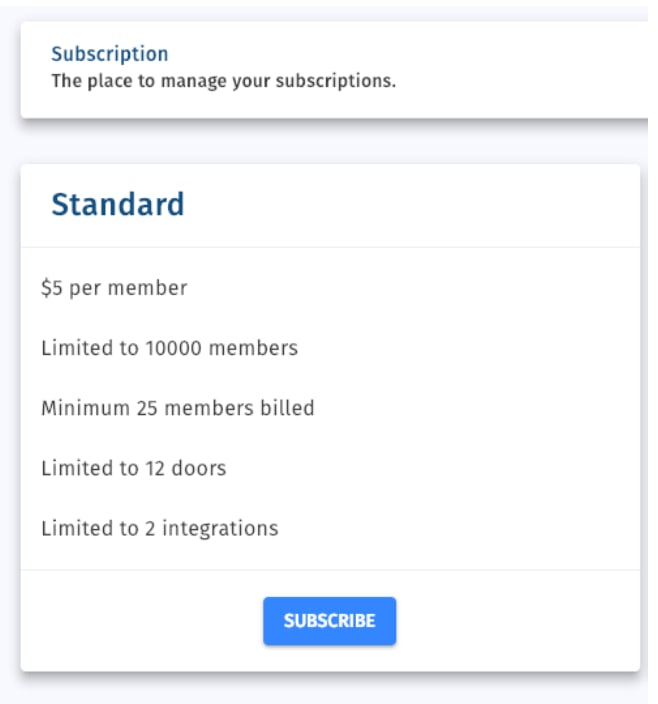
Example of a cloud licensing for access control from the access control dashboard
The Role of Physical Access Control for IT
Learn about future-proof access control with Kisi
Installation and Onboarding Process
Once you’ve settled on a system, picked a provider, completed a site visit, and accepted a quote, you can then move on to the physical installation process, and the onboarding of your team to the system (I am, here, assuming that you went with a modern access control system like Kisi’s, and thus have some web-based component that you need to enable).
Installation
The physical installation should be relatively straightforward: the access control provider should have set you up with a trusted installer who handles it all. Other articles on this academy page delve into greater depth on the specific electronics of the controllers, readers, and locks. Essentially, the installer will put the controller in an IT closer or other secure location, run wires through the walls to the relevant doors, install the electric locks on the doors (if you don’t already have those), and the Kisi readers next to the doors. The wires will be inside the walls and thus invisible, leaving you with a smooth, aesthetically pleasing office.
A guide for a typical access control system can be found on the bottom of this page, and here is a screenshot of an example wiring:
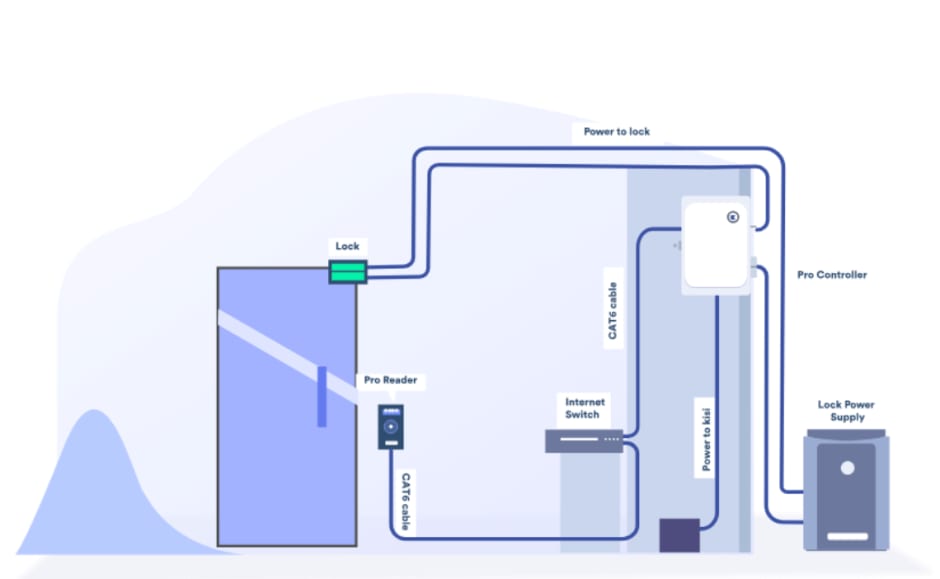
Example installation wiring diagram of a cloud system
Configuration
After your access infrastructure including locks, access control panel and door readers are installed, it’s time to configure those. Using a cloud based system you will just be able to go to your cloud based web dashboard and set up the relays that connect to the corresponding door lock:
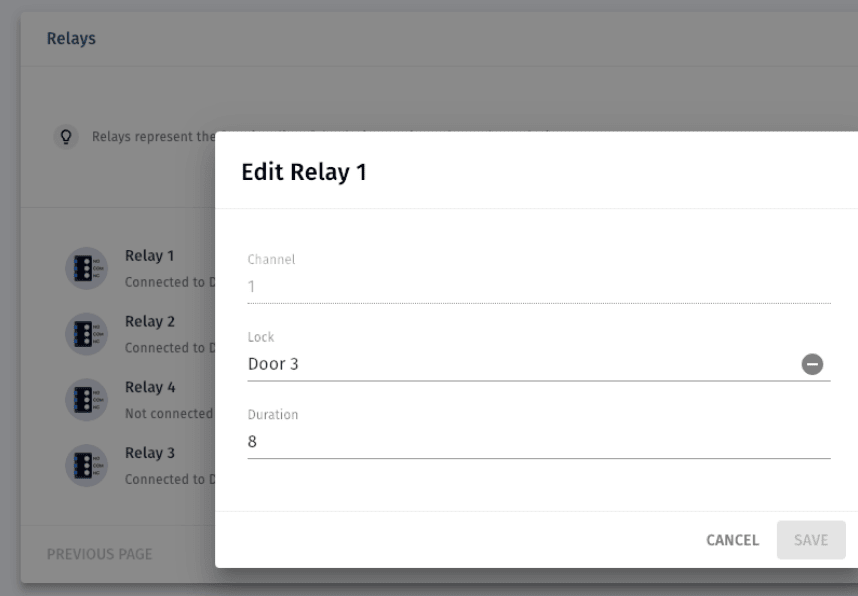
Example of configured door relay to unlock a door including the seconds it should stay unlocked.
Beyond relays there might be other door hardware configured, e.g. door contact sensors and request to exits:
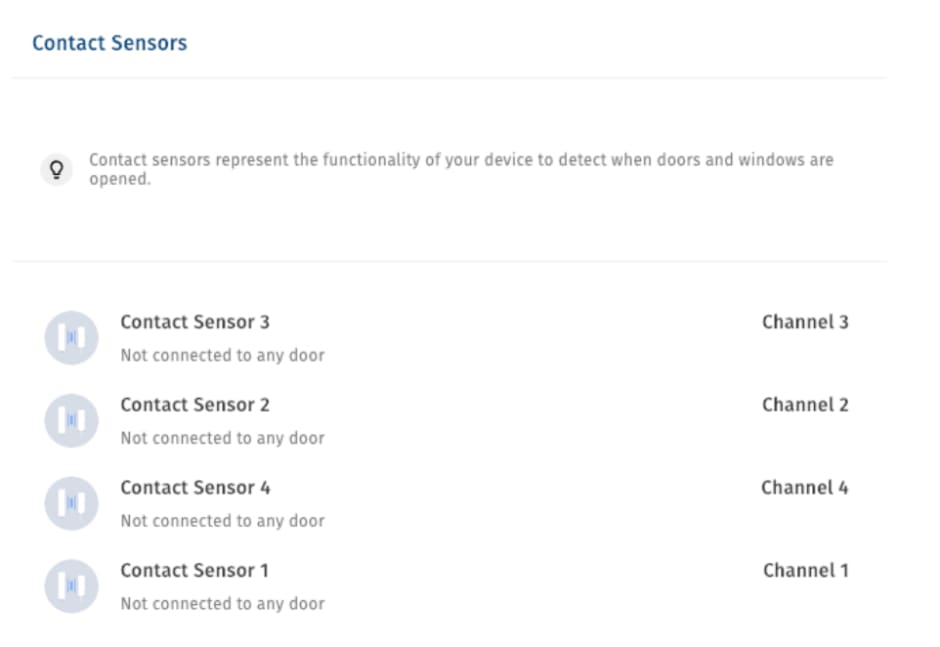
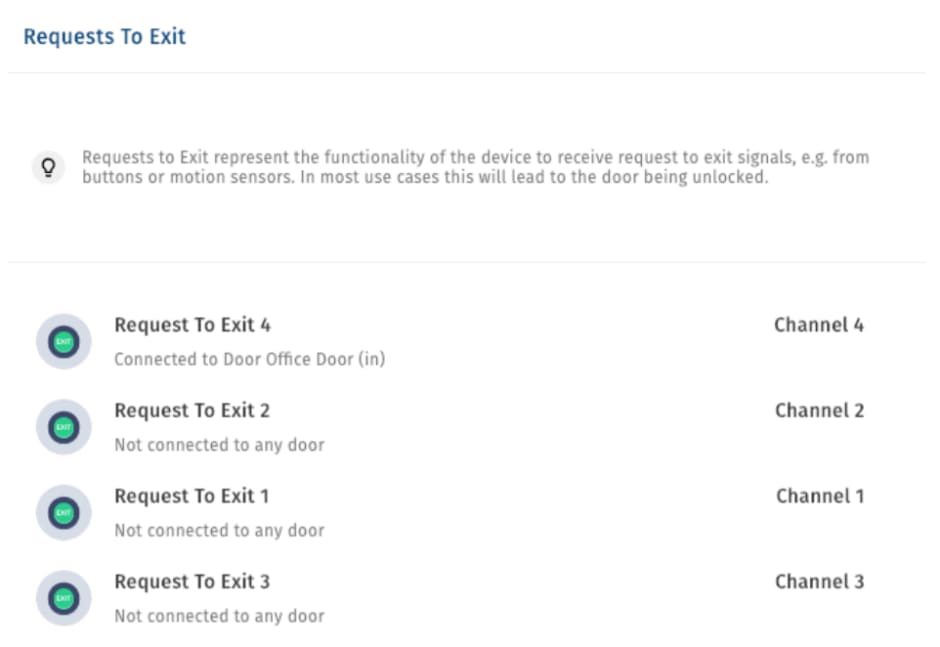
The last step would be to configure the reader. Simply tell the system at which door the reader is physically installed, and you can make sure that this door is actually unlocked when the reader in question is triggered.
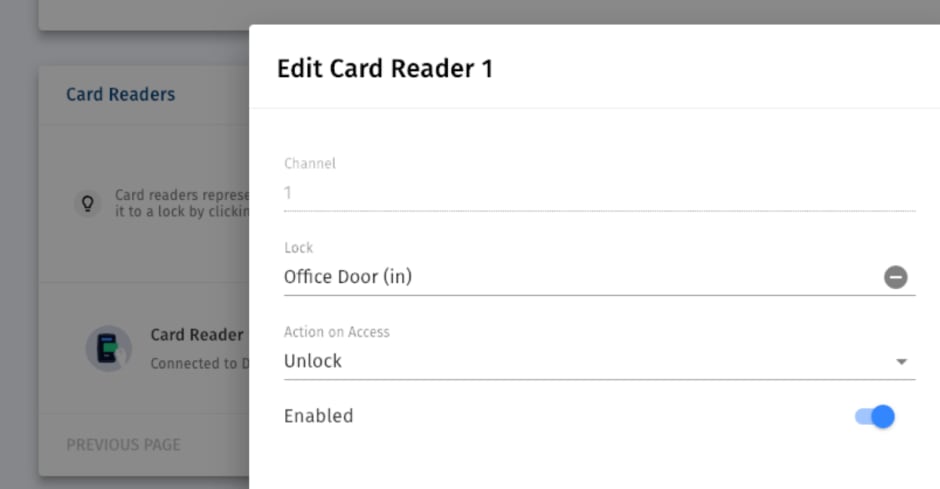
Onboarding
Once the system is tested, announced and approved the fun part begins: The actual roll out. You can start provisioning access for your team. The most important part to consider is that some people will have issues or problems getting access, so make sure to roll out on a day that is not the most critical. Most people choose Fridays so that there’s time to troubleshoot. It’s difficult to give a concise overview of this process, though, as it will vary dramatically based on which type of system you elected to go with. As a general rule of thumb, the more modern the system is, the more elaborate the onboarding process becomes for an IT manager, with the benefit of significantly facilitating the onboarding and daily use process for the end users (the employees of your company). For instance, with a simply lock and key method, onboarding for an IT manager amounts to handing out keys. However, you then have to keep track of which employee has which key, replace the frequently lost ones, and the process of unlocking becomes rather unpleasant.
On the other hand, with a modern solution like Kisi’s NFC and Bluetooth readers, the onboarding process generally becomes enrolling all new members on the web app, and assigning them to their “groups” (each group has different door permissions). Then the employees download the app and create an account, which probably take slightly longer than adding a key to a ring, but thereafter the whole unlock process boils down to holding their phone to the reader. Moreover, the monitoring and offboarding process becomes simple and elegant for an IT manager, as they can do it all from the comfort of their laptop, without having to keep track of physical access tokens.
Again - a sign of quality can also be the help documentation of an access control provider. Here is the onboarding documentation from Kisi.
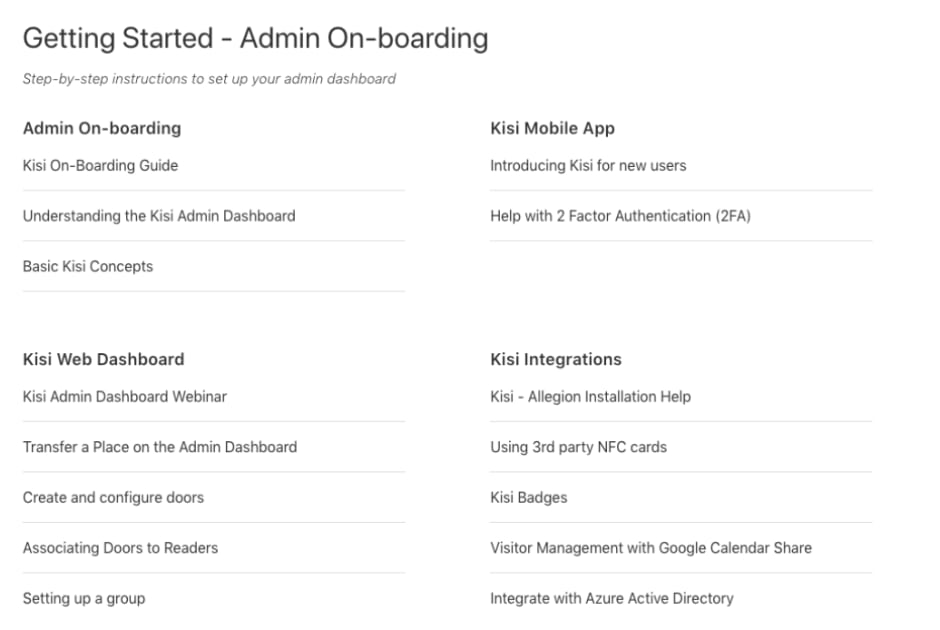
Overview of Kisi’s onboarding help center
Final Remarks
If this onboarding process sounds slightly intimidating, not to worry - any access control company worth their salt will assist you with every step of the process, and provide customer support if ever an issue should arise. For a more in-depth analysis of physical access control methods and the onboarding process, check out Kisi’s detailed physical security guide.
For further assistance in this process, and to get your own state-of-the-art access control system, contact a Kisi rep today!
Save time. Enhance security.
Modernize your access control with remote management and useful integrations.
Continue learning

