In today’s tech-infused world, where almost everyone has a private mobile device, and may or may not use it for work, privacy and data security are becoming increasingly prevalent issues. How can you be sure that your company’s data isn’t being compromised or lost on employees’ personal devices? How do you know if they’ve taken adequate measures to safeguard against hacks or leaks?
To address this issue, many companies either assign their employees company smartphones, or use techniques like Mobile Device Management (MDM) for Bring Your Own Device (BYOD) environments.
Should your company institute an official policy for personal mobile devices?
Deciding whether to establish an official company policy for personal mobile devices can be pretty tricky. While some of the bigger tech giants have the funds and infrastructure to hand out mobile phones to all their employees, for other companies that’s pretty impractical, and can seem restrictive to team members who want to use their own phones. So here we’ll run through some factors to consider when deciding how to implement a less dramatic policy — some sort of device management on personal phones.
Sensitive Data Protection

Of course, if your company handles very sensitive data, you’ll certainly want to protect it. Major data breaches are committed on a global scale everyday from common people's cell phones, not just government emails (e.g. Google, FB, healthcare companies, airlines, etc)
If you have truly sensitive data stored on your phone, like bank account numbers or the like, then you should certainly explore the option of restricting employee data use to secure and encrypted company devices. However, if you’re somewhere in the middle, many MDM softwares allow you to add layers of encryption and protection to the data. For instance, you can simply get a password manager, or a VPN (virtual private network) software that securely connects employees to the company network.
Lost or stolen data can be a very serious issue, and if there’s any chance your company would suffer significantly at such a breach due to a compromised personal employee mobile device, then you should certainly consider an MDM protocol.
Measuring Impact on Organization and Employees
You might also want to consider the impact an MDM system would have on your organization itself, as well as your employees. If you don’t currently use an MDM system, introducing one might be more expensive and time-consuming than the problem demands. You’ll have to update all operating systems and make sure all your machines are networked properly. Of course, best practices for office IT would require you to do this anyway!
More relevant is the impact such systems can have on employees, with respect both to productivity and general team morale. It’s a well-known fact that employees even at the most high-tech companies don’t enjoy switching systems or generally getting dislodged from routine, so you’ll want to make sure that the onboarding and deployment process is smooth and seamless.
Beyond productivity: You should be clear in explaining why exactly an MDM system is necessary to the company, so they don’t feel like you mistrust them. Communication and trust are incredibly crucial to a good working manager/employee relationship, and forcing your employees to install what to them will look like child TV filters could damage that dynamic.
Challenges of Having Multiple Operating Systems
You should also consider what operating systems you use in your office, and how the variety therein could impact the deployment of an MDM system. Most MDM systems are proprietary to a given type of smartphone or laptop — a relevant example is JAMF, one of the industry leaders who, unfortunately, only work with Apple. Other solutions, like Cisco Meraki or ManageEngine support both iOS and Android, but might have different capabilities for both.

While you can certainly find one unified solution for all the devices that your employees operate, it’s important to keep in mind that different operating systems have different requirements, and different apps might have different capabilities to meet those requirements.
Best Practices for MDM and BYOD
If you’ve decided that you need MDM (because, like most modern tech-enabled companies, everyone at your office uses their personal devices!) then this section is for you. We’ll go over best practices, and give an overview of the best software out there for SMB (server message block) protocols as well as larger companies.
MDM Software
For a market overview of some of the better MDM softwares out there, Kisi partnered with Daniel Macias, head of IT at Bugcrowd, one of the leading online security platforms. In this linked blog post, Daniel gives a summary of his experience with MDM, as well as recommendations for systems for companies of all sizes.
SSO on All Personal Devices
One of the most common methods for implementing MDM on employees’ personal phones is with the help of single sign-on software, or SSO. Popular examples of SSO are Okta or OneLogin. These programs add a layer in between the apps you’re using and your computer: basically, rather than having to remember all your passwords, you only have to remember your password to the single sign-on service, and the SSO keeps all of your password in an encrypted storage.
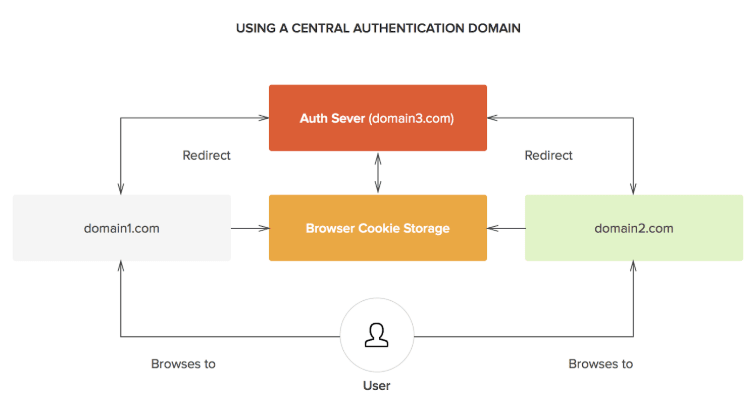
That’s just the basic password manager functionality, though — the best of these SSO services, like Okta and OneLogin, will grant you more functionality, and will help you encrypt and secure all the data that you have on your phone.
That’s why these are so attractive as a base MDM system. They satisfy the security requirement of MDM, but are also unobtrusive and don’t impinge on your employees’ privacy. You can extend the password management and security to all apps related to work: Email, file access (Google Drive), and even physical security, like access control apps.
MDM and SSO for access control—what’s next?
Modern access control apps like Kisi have mobile interfaces, and what’s crucial is that this app will grant you physical access to the space. These apps are also only as secure as the passwords that a user logs in with, and are therefore just as vulnerable to hacking as any other weak password-protected app on your phone.

Meraki MDM can be used to deploy access control, amongst other features, on all employees’ phones
This makes them an ideal use case for SSOs. Modern vendors are working on combining MDM benefits with SSO to provide a seamless experience for all apps on your phone. Many apps like Kisi are enabling their apps to communicate via SAML, a totally secure language used to transmit authentication information, and the base of all modern SSO providers. It’s a very natural use case: just as you want to protect your virtual data, you likewise want to protect your physical space, protecting the data for physical security on your phone.
Main Takeaways
Though there may be concerns about personal device privacy, and onboarding with multiple systems might be challenging, it’s still probably a good idea for you to explorean MDM system if your employees have a tendency to use personal devices for work-related activities. From protecting sensitive emails and files, to adding a layer of encryption to your physical security, MDMs and SSO providers can go a long way to increasing security at the office.
Save time. Enhance security.
Modernize your access control with remote management and useful integrations.

