In another article this series, we went over the general feature of mobile unlocks and reviewed the landscape of mobile apps for access control, with the various features and functionalities you might find. In this article, we’ll take a closer look at the world of iOS and explore how mobile unlocking works on an iOS app, along with the various particularities of Apple iPhones.
If you just want a quick overview, here is a video from Kisi TV that outlines what we'll be discussing:
How does Bluetooth work on an iPhone?
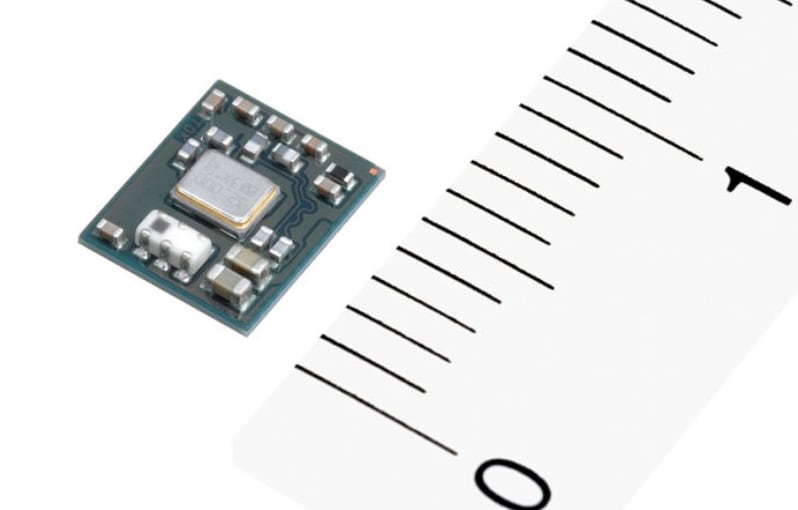
iPhones, like all modern smartphones, come equipped with a standard Bluetooth chip. These chips emit signals in the radio wave range and turn your iPhone into a sort of RFID emitter. For a more in-depth explanation of Bluetooth technology, please visit this article. Specifically, iPhones have chips that adhere to the BLE (Bluetooth Low Energy) standard—the phone loses nothing in functionality while conserving more battery. Here you’ll find a picture of your typical smartphone Bluetooth chip—note that those distances are in centimeters, not inches!
iBeacon Technology
Around 2013, Apple developed a new standard for BLE technology that it named the iBeacon. The iBeacon protocol sets definitions on how iPhone BLE chips should be manufactured.
Among other things, the iBeacon decreases power consumption, increases strength of Bluetooth connection between iPhones and increases the accuracy of an iPhone’s indoor location tracking (a feature that GPS famously struggles with). Think about how many times Google or Apple maps lost track of your position when you were in a building! Modern access control apps utilize this iBeacon tech to its full extent through leveraging the more precise positioning it permits.
Mobile Tap to Unlock With Bluetooth
From years of being in the business, and common sense, we know that the easiest use-case for unlocking your door with your phone is to simply tap it to the reader (much as you would a keycard). No need to fumble around your wallet, or dig around in your backpack: Odds are your phone is already in your hand, anyway.
How does tap to unlock work?
The phone will monitor the iBeacons that the reader advertises. So when the phone is nearby the reader, it will start the app in the background and be ready to perform unlocks over BLE.
Without location permission, we have to rely on iOS to start the app based on the BLE service it advertises. Which in our tests has been slower and sometimes doesn't happen at all.
Under what conditions will it use background location service, how long will it continue using location service, and will it consume a lot of power?
We don't use the location services (meaning GPS) at all. But Apple has decided to put iBeacons under core location, hence requiring location permission, although iBeacon is BLE.

Bluetooth interference?
As you can imagine, access control is not the only application on your phone that will use the Bluetooth chip. There are probably a dozen devices in whatever room you’re in right now that are all trying to ping your Bluetooth chip for a signal. So, the question of whether they might interfere with each other and cross wires is a natural one.
We’ve covered the issue of BLE interference more in depth, and explained the science behind it, in another article in this series. Please refer to that for a deeper dive. However, for the purposes of access control, you can rest assured that there will be no crossing of wires, or mis-transmission of information. The reader uses Bluetooth fencing (more on that later in this article) to only communicate with your device when it’s close enough to transmit information clearly and fully, without loss or corruption of information.
What about the NFC chip?
We commonly get questions from iPhone users about why they can’t use the NFC chip to unlock their doors. As we covered in this article, NFC tap to unlock is faster and more reliable, despite the fact that its range is more limited; and, like all modern smartphones, the iPhone comes equipped with an NFC chip. So, why shouldn’t you be able to use your iPhone as an RFID/NFC card?
The answer here is deceptively simple: Apple is proprietary with their tech, and don’t let third-party applications use the NFC chip for transmitting. They do allow developers to read a (very restricted) subset of NFC tags from outside objects, but the application process for the use of this chip is long and unnecessarily complicated. Most of the time, these applications are not considered and widespread use of the NFC chip remains restricted to one functionality: Apple Pay.

Touchless Access Control by Kisi
Discover what makes Kisi the most advanced access control system.
iPhones and Access Control
In this section, we’ll take a closer look at the particularities of iPhones in the world of access control, and how they’re different from Android-based unlocks.
In-App Unlock vs Tap To Unlock
There will be two main methods for unlocking with most iOS access control apps: Tap-to-unlock, where you hold your phone to the reader (covered above), and in-app unlocks. For the latter, the interface will depend on the specific app you’re using, but generally you’ll have something like a list of all your doors neatly organized on the screen and you can scroll to each and unlock it using a combination of WiFi and Bluetooth connectivity.

BLE Beacon Fence vs Tap to Unlock BLE Range
Many applications will actually limit the distance at which a device can perform an unlock. This range, however, will be different for the in-app unlocks and the tap to unlocks, despite the fact that both use Bluetooth connections.
Bluetooth transmitters can establish a sort of geofence around them where their signal reaches. For BLE (Bluetooth Low Energy) devices, this is limited to around 50 meters, but can be artificially reduced by programming it to a shorter distance.
For in-app unlocks, the reader will continually transmit a signal and as soon as it picks up another Bluetooth chip it will establish a weak communication with it just to determine its approximate distance. If it judges the device to be within the accepted range, then it will allow certain functions to be performed, namely unlocking the door.
As an admin for a Kisi ‘place’, you can activate a Bluetooth fence on the reader. It will use its Bluetooth Beacon capabilities to only allow devices within a preset Bluetooth range to use the swipe to unlock functionality.
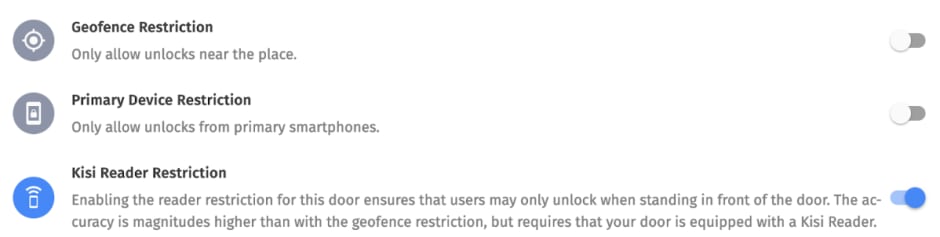
A similar process is used for tap to unlock, but here it’s actually set by Kisi for security and strength of connection reasons. Kisi (and other similar apps) will set a maximum range on the tap to unlock, in order to prevent accidental unlocks or unwanted strangers piggybacking on nearby BLE signals, in order to gain access to the building.
Wearables—BLE in the Apple Watch
The market for wearables is booming, and it’s rare these days to have a modern office without at least one Apple Watch in it. As a result, many access control companies are starting to integrate with these wearable techs and develop solutions to deploy their apps in the different interface.
For instance, with Kisi in particular, you can receive a notification to unlock from within your Apple Watch and swipe its screen to unlock your door. With the spread of wearables into the Internet of Things market, it’s a safe bet that we’ll see a lot more access control in Apple Watches in the near future!
Closing Thoughts
Using BLE and iBeacon technology, Apple has given access control apps the tools to develop a versatile and powerful suite of tools to secure your space. With both tap to unlock and in-app swipe to unlock functionalities in iOS, apps like Kisi are changing the way you access and secure your space.
Save time. Enhance security.
Modernize your access control with remote management and useful integrations.

