What is a keycard? How does it work in access control?

Keycards get called many different names, mainly based on the type of card. Often referred to as prox cards, swipe cards, and fobs, sometimes magnetic cards, RFID/NFC cards, and even simple ID cards. Despite the different names and the technology they use, their function is always the same: To efficiently and securely grant or restrict access to a specific area.
Maybe you've heard of HID cards? Historically, the main provider of keycards, HID Global, manufactures, distributes, and sells access cards using their proximity readers. Despite the popularity, a major problem of certain types of HID keycards is that they can be easily hacked using $10 devices. That’s because most common cards run on the vulnerable Wiegand protocol, which allows hackers to copy cards and keycards quickly and inexpensively. To lessen this security threat, you can add two-factor authentication or layer mobile access control. Keep reading to explore all the main types of access card systems and compare them with other modern access control options.
You can copy HID cards within seconds with the Flipper Zero or calculate the facility codes most of these cards use with free facility code calculators.
Kisi, as an advanced access control provider, doesn’t recommend or condone keycard copying or theft. We want to keep you informed and vigilant by displaying the vulnerabilities of popular access systems. Let’s dive into all the keycard systems ins and outs.
How do cards work with key card readers?
A keycard is a security credential or token that grants you access. These systems require a keycard reader (installed on the door) to work so that you can gain access by either tapping your card on the reader (proximity reader), swiping it (swipe reader), or inserting it (insert reader). With a keycard reader, you no longer need to insert a metal or traditional key into a tumbler lock to gain access. What is a card reader? The part of the access control system that recognizes the keycard (the embedded access credential on the keycard magstripe or a chip in the card itself) and then communicates with the door lock each time you attempt an unlock.
How does the card reader communicate with the door lock?
The access control reader is wired to an electric lock on your door and will signal the lock to start an unlock event. If the reader recognizes the unique code on your card, permission is granted for access. If not, then access will be denied. With a good access system, like Kisi, the whole process takes less than a second.
Advantages and disadvantages of keycard entry systems

Understanding how access cards work, we can look at the pros and cons of choosing a keycard system over more advanced types of door entry systems.
Can provide restrictions for certain times, certain access levels, or even certain numbers of unlocks.
A physical token is still required, making door access less convenient and more prone to security vulnerabilities.
Provides remote deactivation capability, making cards a more secure door unlock method than keys and keypads.
Losing your keycard still compromises access to your space. Cards are much easier to forget or misplace compared to mobile phones we always have at hand.
Cards and key fobs fit perfectly into your wallet, card holder, or keychain.
Many keycards can be easily hacked using inexpensive devices, requiring an additional layer of security.
Can be reused by reconfiguring access using the same card. Old access cards can be decommissioned, unlike metal keys that need to be returned.
Growing the business and hiring new employees requires buying additional keycards. Mobile access solutions are more sustainable and scalable.
Most keycard systems can be easily upgraded to the cloud to enable mobile access and enhance security with Kisi.
Mobile access methods allow a more seamless unlock experience since users don't need to fumble to find the card and can unlock doors even when their hands are full.
Keycard entry systems alternatives

Given the disadvantages of keycard entry systems, modern businesses need to identify better alternatives to enhance security, streamline operations, and enable seamless user experience. Most companies choose standalone or integrated mobile access solutions to accomplish business goals and empower both users and admins.
Users enjoy mobile door entry and don't have to worry about forgetting or losing their keycards or fumbling through bags and pockets to unlock. Using the RFID and Bluetooth chips inside the phone, you can use your phone as you would an access card and tap it to the reader to unlock it. With Kisi's MotionSense technology, you can enable a more hygienic, touch-free access experience and allow users to unlock doors by simply moving their hand in front of the Kisi reader. There's, of course, the option to keep the keycards so that users can unlock doors with both their cards and their phones.
Management and admins reap the benefits of having a cloud-based access system (as opposed to a legacy local-hosted system). The remote global management from a single pane of glass enables admins to manage access to all doors and locations wherever they are, even from the convenience of their phones. Kisi hosts and securely manages all the data, maintains and future-proofs the products with over-the-air updates, and offers advanced insights and reporting to support making data-based decisions.
Contact our team to experience the ease and security of a modern cloud-based mobile access control system.
What are RFID/NFC keycards?

RFID cards are access credentials most widely used in commercial office spaces. These cards (sometimes referred to as 'tags' or 'fobs') can be classified by the range they communicate (low or high) and the way the communication happens with the reader (active or passive). RFID stands for “radio frequency identification,” emphasizing the essential technology behind them. They emit identification information in the radio frequency range, and the access reader will pick up those signals and authenticate them.
NFC is a set of standards over RFID technology. NFC cards, short for “near-field communication” cards, are RFID cards that operate over a specific frequency and have a clever bit of engineering that allows them to communicate quickly and securely over short distances. Read our guide that compares RFID and NFC access control systems, explains the technologies and applications, and highlights the benefits and drawbacks.
How are permissions encoded on a magnetic keycard?
Keycard systems often come with a key encoding machine, which you can use to configure the permissions granted to the specific cards. The system should allow you to grant permissions for multiple doors, configure the date and time for access, and even the number of times a user can access the space.
All these details are built into a highly complex algorithm written into your keycard’s magstripe. This magstripe contains thousands of tiny magnetic bars. Each can be polarized either north or south. Polarizing these magnets creates a sequence that is encoded on your card.
There are other ways to encode a keycard, usually used for corporate spaces. These include newer models with radio-frequency identification (RFID), or “smart cards,” which contain an embedded microcontroller to handle security. We'll cover RFID keycards and modern assignment credential methods below.
RFID and NFC keycard frequency ranges
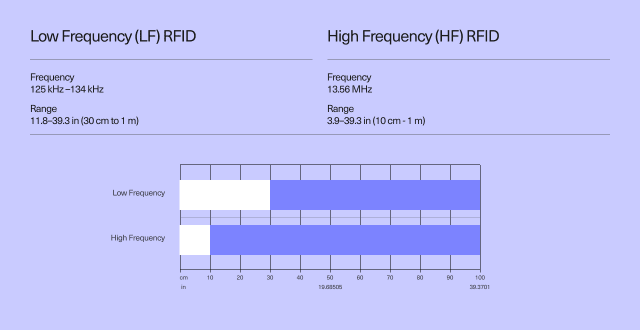
RFID readers can operate on different frequency ranges. The frequency is measured in Hertz (Hz) and refers to the number of times per second that the electromagnetic wave emitted by the credential repeats itself. The keycard frequency determines how far the signal can travel and how much data can be sent.
Credentials can be low-frequency (LF) or high-frequency (HF), depending on the application requirements and the specific technology used. The lower the frequency, the less data can be sent, but the signal can travel farther. The higher the frequency, the more data can be sent, but the signal can’t travel as far.
- Low Frequency (LF) RFID systems operate at a frequency of around 125 kHz - 134 kHz and have a range of 11.8 to 39.3 in (30 cm to 1 m). Low-frequency RFID systems are used for various applications, including supply chain management, inventory tracking, and access control.
- High Frequency (HF) credentials operate at a frequency of 13.56 MHz and provide distances between 10cm and 1 meter. Examples of access cards that use HF RFID are NFC cards, which include smart cards like MIFARE. NFC is building upon the standards of high-frequency RFID, and it is considered a specialized branch of RFID technology. The uniformity of communication allows NFC card manufacturers to make the communication more secure and more efficient.
Due to the added security and encryption enabled in NFC rather than simple RFID, NFC technology is also used on credit and debit cards for contactless transactions. Some modern access control providers, like Kisi, now support these third-party NFC cards to unlock doors secured with smart readers.
Now that we covered the different types of RFID frequency, there is another parameter to consider. RFID can be distinguished into two broad categories: Passive or active tags (or cards).
- Active RFID tags have their own transmitter (and power source). Active RFID tags are used for cargo, machine, or vehicle tracking.
- Passive RFID tags do not require a battery. The reader on the wall sends a signal to the tag. That signal is used to power the tag and reflect the energy back to the reader.
Proximity cards are often low-frequency, 125kHz, and fall under passive RFID cards, given they cannot get power.
How do RFID keycards work?
Passive cards have three components sealed in the plastic: An antenna (mostly coil or wire), a capacitor, and an integrated circuit (IC), which contains the user’s ID number. The RFID reader on the wall has an antenna, which continuously emits a short-range radio frequency (RF) field. When you hold the card on the reader, the card absorbs the energy from the RF field generated by the reader—the technical term is that it's an induced current. This energy creates (induces) a current powering the integrated circuit, which in turn makes the chip emit its ID number. The reader sends the ID back to the server closet or IT room, where the main access control system panel usually resides. The sent ID signals that the user wants to unlock the door. The format the reader communicates in is often the Wiegand protocol.

How do Kisi keycards work?
Kisi offers three physical credential types with high-frequency (HF/NFC)
transmission. Each Kisi keycard has a token associated with it, printed on
the front. This token helps admins to assign a card to a user and
accurately and securely track unlocks as users enter Kisi-secured spaces.
Tags are adhesive square-shaped stickers that you can add to existing
access cards that are not NFC enabled. Fobs don’t have buttons and work
the same way as a keycard, communicating with the reader using NFC
technology.
Kisi
card keys can be assigned
with three different methods:
- Manually adding them by token or card number
- Scanning the cards at a Kisi reader
- Scanning the cards with the Kisi Android app
The Kisi access system also supports third-party NFC cards in unique (UID) mode that admins can assign by scanning at a Kisi Reader or with the Kisi Android app. Kisi can also work with all low-frequency RFID (125 kHz) card types. Yet some card types may not be supported by Kisi since they don’t comply with NFC standards.
Besides supporting and upgrading your current access system, with Kisi, you can also enable mobile credentials to work in sync with your keycards. Contact our team to see how Kisi can work for your use case.
Swipe cards for access control

Swipe cards or magnetic stripe cards work by storing data in a magnetic layer placed on the card that can store data by altering the tiny magnetic particles. By pulling through or swiping the card through the magnetic reader, the stored data is confirmed, enabling the card access system to work.
Besides being used as access cards in the physical security industry, swipe cards are also used in credit card payments or identity verification.
A swipe card door access control system was a common security solution for large organizations that must continually let in and out the same employees. Although the magnetic stripe is the key differentiator, swipe cards can contain additional means for storing, reading, and writing data, such as RFID tags or microchips. Swipe cards are a convenient and affordable solution to control access. Still, they usually provide limited security protection and convenience that needs to be supported by extra technology or authentication factors to suffice for top security requirements.
How do swipe cards work in access control?
Unlike badge entry systems, magnetic swipe card access systems use magnetic strips at the back of the card to encode data. The magnetic reader's head reads the data when you swipe the card through it and enables access.
This is one of the most common technologies used when shopping for groceries, pulling cash out of an ATM machine, or presenting your license as an ID document at specific locations. When the card access system is made of a standalone reader, all swipe cards will be connected to that single access control device. This is rarely the case, though, as most organizations need either more cards or require additional security which can be obtained from several units distributed in a network. Network or PC-based card access combines multiple magnetic readers in a joint software that can be used to monitor the access events from all readers from a central point.
Advantages of swipe card entry systems

Swipe card access control systems have some advantages that make them convenient for access control over other access credentials, such as RFID or NFC (proximity) cards, smart cards, or combination cards:
- Swipe card access is cheaper than other technologies. The technology to store data in magnetic cards can be used in hundreds of cards at a low cost.
- Magnetic cards are interoperable. Unlike some RFID devices, which use radio frequencies to connect devices and can incorporate a range of frequencies, you can use the same swipe cards in different use cases since they are based on the same technology. For example, using your credit card to unlock doors.
- The invader must physically possess the swipe card to compromise the magnetic stripe and steal data. Most attacks on swipe card data compromise ATMs’ readers or suppliers’ stored data records. For RFID or NFC cards, violations can be made with interception and interference, and the attacker doesn’t need to get to the card.
- Swipe card access is read-only. Owners can use it only in passive mode, without writing capabilities and changing the data in a system. Smart cards, on the other hand, use both reading and writing modes.
- Magnetic stripe cards enable individual tracking and audit trails.
Disadvantages of swipe card entry systems

As the most simple and traditional access control method, swipe card access control has some disadvantages over the alternative forms of access control.
- Swipe cards can be unreliable. Sometimes, the magnetic stripe can get damaged or corrupted, making the data unreadable and creating difficulties for the person using the card, who will have to swipe multiple times until the data is read properly.
- In general, magnetic access cards are considered less secure than the alternatives because it takes less advanced technology to copy the device data and misuse it for theft or identity theft. These cards are basically most similar to mechanical keys.
- Magnetic cards cannot cover a range of industries. For example, NFC is increasingly present not only in access control systems but also in finance, mobile payments, transport, redeeming rewards, and many other consumer uses.
- Swipe card access systems cannot provide multi-technology authentication unless they are upgraded with additional access control tools.
Key fob entry systems

A key fob is a type of access keycard or security token. It acts as a wireless security device that allows users to access their buildings, offices, and cars. Key fobs are usually utilized for locations with high people flow yet still require entrants to authenticate their access. Authentication is done by initializing the built-in security access system each time the fob is activated.
Key fobs are mostly used for residential real estate, like apartment buildings and condominiums, but are still in use in some commercial buildings to secure common entries of multi-tenant buildings or specific offices. Fobs often contain an RFID tag, which operates similarly to a proximity card, which communicates access credential information (via an access reader) with a central server or cloud-based access panel located in the building.
You can program key fobs to allow time- and location-restricted access to secured areas. Locking and unlocking a door with a key fob usually only requires you to push a button on your fob or tap the fob against the access reader. Some key fobs provide two-factor authentication where a user has a personal identification number (PIN), which authenticates them as the device's owner.
Key fobs are an integral component of keyless entry systems, especially in the automotive industry, where they are used to unlock your car door from a distance. However, similar to cards, it still requires a physical object to be issued to users before they can begin electronically unlocking their doors. This means that losing or forgetting your key fob is still a very real possibility that would prevent you from accessing your space and undermine the security of your office, building, or car.
How do key fobs work?
The key fob (or wireless remote) usually operates in conjunction with a reader and an electronic lock (e.g., an electric strike). The key fob communicates with the reader using radio wave signals—RFID technology. The reader receives the ID information from the fob, authenticates it, and, in turn, relays an instruction to your door lock to perform an unlock event if the credentials are authorized.
Both the key fob on your keychain and the access control system have memory chips that allow the fob to work. When you press the fob button, it sends a code to the door lock with instructions on whether the door should stay locked or it needs to unlock. If the code sent to the access control system matches, it will perform that action and unlock the door. The code is randomly generated each time the fob is used.
This code utilizes a 26-bit Wiegand protocol when communicating instructions from the fob to the system. It is a binary code with 256 different possible combinations per fob, and there can be up to 65,535 ID numbers that would work for each code. Matching each code with each ID, you can issue up to 16,711,425 fobs without ever duplicating a user. Programming the key fob is essentially ensuring that the access control system and the fob are synchronized so that the door recognizes the codes the fob is sending.
The transmitter’s frequency determines the maximum distance that will allow the key fob to send a code to the door. Quick note: If your fob only works when you get near the access badge, it might be utilizing a simple coil, e.g., a 125kHz’ transmitter’. Therefore, it only works near the transmitting coil as the magnetic field decays very fast.
Experience seamless mobile and card access with Kisi

Mobile access, keycards, or encrypted fobs? With Kisi, you can choose the solution that works best for you or even allow different types of credentials to work at the same time. For example, keep your current keycard system and enable mobile access for a frictionless access experience.
Regardless of which type of credential you prefer or whether you are deploying a completely new or upgrading your current system, Kisi enables you to leverage the benefits of a cloud-based access system. Global management, remote unlocks, health monitoring, granular access permissions, scheduled unlocks and automated rules, audit trails, advanced reporting, integrations with third-party software and hardware, access to our API, and a lot more. Contact our security experts to help you find the right access solution for your needs. Explore why modern businesses worldwide choose Kisi to manage physical access.
