Smart cards in access control #
A smart card is a typical plastic card that contains an embedded computer chip which is either a memory or a microprocessor type. The data the chip responsible for storing and transmitting is connected to value, information, or a combination of both. This data is both stored and processed within the card’s chip. The card data is transmitted via a reader, which is the outward facing component of the smart card security computing system.
Several systems across a wide range of commercial sectors, like banking, healthcare, finance, entertainment, and media, nowadays use smart card security systems in their applications. Applications using smart cards benefit from the several security features these chip cards provide. The efficiency of the systems is elevated to a large extent due to the smart cards.

Necessity and application of smart card security #
The need for convenience and security of any transaction has made the deployment of smart cards an asset. One of the primary uses of smartcards is providing safe storage of confidential information, like account identity.
In general, smart cards are preferred to other machine-readable cards, as they come with much lower maintenance costs. Also, unlike other card security systems like magnetic stripe cards, smart card security systems put all necessary information on the card itself. Magnetic stripe cards divide the information and function load between themselves and the reader or central server. Thanks to this, the user does not need access to obscure databases during transaction processes.
Smart cards also facilitate the secure transaction of data through any type of virtual network. Unlike the magnetic stripes, which store negligible amounts of read-only data, smart cards are fitted with microprocessors which enable the cards to receive, store, update, and make decisions about data.
This means that if you’ve been issued a smart card, but your information gets updated, you don’t need a new card and can instead update the information right on your existing card. This greatly reduces the risk of losing your card or misplacing the old one and compromising your security.
Also in terms of security, smart cards protect against a wide array of security threats starting from careless storage of user passwords to intricate system hackings. In a fully online system, users are often careless and misplace or share their passwords, meaning they have to change them often or risk getting hacked. Resetting passwords is a highly expensive task for an organization. Smart card security systems offer a highly cost-effective solution for this issue.
The most relevant applications of smartcards can be categorized in the following way:
- SIM cards and telecommunication: Subscriber identity module, required by all phone systems under the global system for mobile communication, is the most commonly used application connected to smartcards. The smart cards are configured to enable the unique identifier, which is stored in the SIM card, to protect the rights and privileges of each mobile subscriber.
- Loyalty and stored value: Smart cards are used as a tool of stored value, particularly in loyalty programs across various sectors like transportation, parking, and retail, which track data and offer incentives to hold onto their customer base.
- Securing digital information and physical assets: In addition to providing information security, smartcards are also used to safeguard services and equipment by restricting access only to permitted users. Delivery of digital information and entertainment services is encrypted and decrypted via the smart card of each subscriber base. Smart cards have also proved to be useful tools for machine and equipment settings in sensitive laboratories.
- E-commerce: Smart cards facilitate the process of e-commerce transactions by enabling consumers to securely store relevant information about purchases. For instance, the smart card stores details of personal accounts like credit balance as well as preferences and purchasing trends of consumers. Smart cards can be used for micro-payments as well as for management of expenses.
Types of smart cards #
Smart cards can be divided broadly into three categories, depending on the technology of the security chip they contain:
- Integrated circuit microprocessor cards: Also known as chip cards, microprocessor cards offer far greater memory storage and data security than traditional magnetic cards. The current generation of these cards operates on an eight-bit processor, 16 kb ROM, and 512 bytes of RAM. These cards have built-in data processors, all included in the smart chip. As a result, these smart cards are primarily used for security digital identities (identification cards) and are implemented in applications that require manipulation of large quantities of data. That means that if you need to store and update real-time a large amount of data on a card, like all the particular identification data of an employee, this is an appropriate smart card security system. This particular card can add, delete and alter information on the card. Some examples of these cards are stored value cards or cards that safeguard cell phones against fraud.
- Integrated circuit memory cards: These cards can hold up to 1 to 4 kb of data, but have no data-manipulating processors on them. Thus these cards rely on an accessory card-reading device for the purpose of processing data. The memory card can be used only in the case of a pre-established task. Prepaid phone cards are the most common example of this type of smartcard, as their sole purpose is to add a fixed amount of value to a phone with fixed hardware inside of it. It doesn’t need to be updated or have its data changed. These smart cards are not often used for security systems.
- Optical memory cards: Optical memory cards store up to 4 mb of data, or several orders of magnitude, more than integrated circuit cards. However, once the data is written, it cannot be deleted or replaced. This makes them optimal for storing large amounts of data you want to access in the future, but that you will not need to modify in any way. Optical memory cards are ideal for applications that entail recordkeeping, like medical files.
Structure of the chip of a smart card #
The chips of the smart cards are manufactured from silicon wafers, attached with aluminum contact areas, coated in an epoxy resin, and embedded inside the plastic cards. The efficiency of the smart card depends on the proper functioning of the chip.
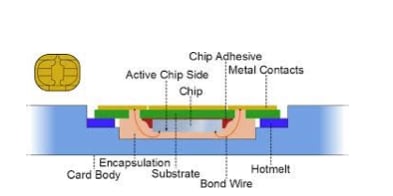
Internal structure of a smartcard #
Smart cards operate on the power supplied from an electrical connector inside a card reader or indirectly from the radio frequency transmission of contactless readers. A smart card consists of the following functional components:
- Central processing unit: It interprets and delivers per the instructions transmitted by the operating system.
- Read-only memory: This type of memory stores data that, once written, cannot be changed or deleted. Manufacturers of the card’s chips fit the card’s OS along with various diagnostic functions on the ROM component.
- Random access memory: The RAM is capable of storing and modifying data and can be accessed as long as its power is being supplied.
- Application memory: Electrically programmable read-only memory (EEPROM) enables the storing and modification of data well.
Security technology in smart card #
Technology and security are closely associated. The ability of smart cards to self-contain data makes them immune from external attacks. There are 3 different types of smart card security:
- Communication with the outside world, such as interaction with a reader, access controller, or server
- Hardware security — these smart cards (or rather their chips) are installed on sensitive equipment and monitor the environment for risks
- Operating system — these are the smart cards that contain authentication information and that you can use for multi-factor authentication in a smart card security system
Markets that have been traditionally using machine-readable card technologies like barcodes and magnetic stripes are increasingly adopting the use of smart cards. This conversion is done after the return on investment is accounted for by each card user year after year. Smart cards are most often used in applications which strictly require security and substantiation.

