What is Intrusion Detection? #
Access control and intrusion detection is a unified system that allows users to monitor and control physical access to certain areas. This form of protection can extend to physical properties and into cybersecurity. Despite access control and intrusion detection being two separate hardware and software components, together they provide effective security measures.
Access control is responsible for restricting and granting access to specific people into particular areas. The goal of such software is to minimize unauthorized access to places, assets, and systems. This is where access control and intrusion detection in cybersecurity comes into play.
Intrusion detection relies heavily on identification and authorization. This means that users can only access restricted areas or devices through proper identification and level clearance. For this reason, we often see the software being guided by regulations and legal requirements.
Intrusion detection systems (IDS) are responsible for ensuring that no violations occur. There are a number of categories that fall under this component with a physical intrusion detection system being one of them. Other categories include:
- Network Oversight
- Host Monitoring
- Anomaly Detection
- Signature-Based Detection
When IDS and access control work together, users can control set parameters for authorized access into both physical and cloud-based locations. A server is used to connect a number of access control components, such as locks, doors, turnstiles, motion detectors, alarms, and sensors, to create a unified security system. Access control helps establish a baseline of normal activity, while intrusion detection identifies and implements secure operations.
How Does Intrusion Detection Work in Access Control? #
When looking at how this system works, it is important to separate it into two functions: a physical intrusion detection system and access control, and intrusion detection in cybersecurity.
IDS access control’s main aim is to detect anomalies in both the cloud and physical space. These systems work by looking for signatures of known attacks in cyberspace or unauthorized visitors. Once these deviations have been assessed, they are examined and the correct protocol is implemented.
In short, intrusion detection works by deploying the following processes:
- Comparing system files against malware
- Scanning for signs of harmful patterns
- Monitoring user behavior for malicious intent
- Monitoring system settings and configurations to ensure optimization
With this in mind, safety has come along way over the past through years and it’s clear to see why it’s popular in the cybersecurity space. Intrusion detection access control is a complete web-based solution where users can enjoy monitoring their intrusion detection system from any device. Cloud-based systems are also available to solely act as physical intrusion detection systems to secure important data.
In the past, intrusion detection access control faced a number of limitations that affected the user experience. These days, users can view and control all system functions from one screen through the support of wireless technology.
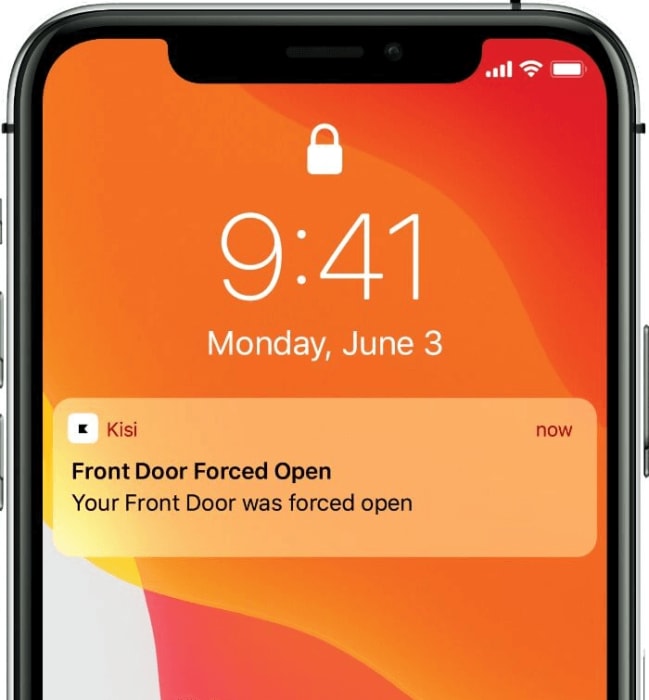
Benefits of Using IDS Access Control #
Not only does utilizing an intrusion detection access control system mean that you’re optimizing your security but it also means that you have access to modular and scalable software. This hardware can easily integrate with third-party programs to ensure that your data is fully protected. You can even look at adding in peripheral components to fit your business or personal requirements.
Due to the flexibility of these controls, users can choose which type of software they’d like to operate. These options include having it installed on-site, watching video playbacks, monitoring intrusion alarms, and recording events from one location - the dashboard. Should you be worried about the security of this data, it’s all backed up in the cloud with guaranteed encryption to ensure its protection.

