A web-based access control system has the technical means to provide remote access control and management. Such a system uses Internet protocols (IP) to communicate signals and data. An IP-based access control system is operable both as a hardwired platform and as a wireless solution.
A web-based physical access control system provides an additional layer of security by automatically collecting data on all events that occur within the system. You can check the security events log from anywhere and anytime and adjust most of the system’s settings remotely.
In fact, a web-based access control system is able to cover entry points located in any part of the world, and you can control multiple sites at once. A reliable platform enables global access control management from a single location using a secure network to control any entry point across the network.

How does a web-based access control system work? #
Web-based access control systems can incorporate both cable and wireless networks to manage readers and locks. Moreover, a technology known as PoE (Power over Ethernet) uses connections that provide power and data to a connected device through a singular cable. This means you can power and manage a security device over a single connection.
What are the different types of access control systems? #
There are essentially three types of access control systems. These are PC/Server software-based, browser-based, and cloud-based systems. The former is the oldest technology in the field of access control systems, browser-based systems and web-based apps have been on the market since the late 1990s, while cloud-based systems emerged more recently.
You can operate a web-based system through any browser and on any device that interfaces with your internal computer network. These systems usually support all the widespread browsers like Firefox, Chrome, and Safari.
You need not install any special software, and your access control software runs on a system controller, such as a modem. You access the device via the browser, and from there, an operator performs all the required tasks and adjusts settings.
Premises-based vs. web-based access control systems #
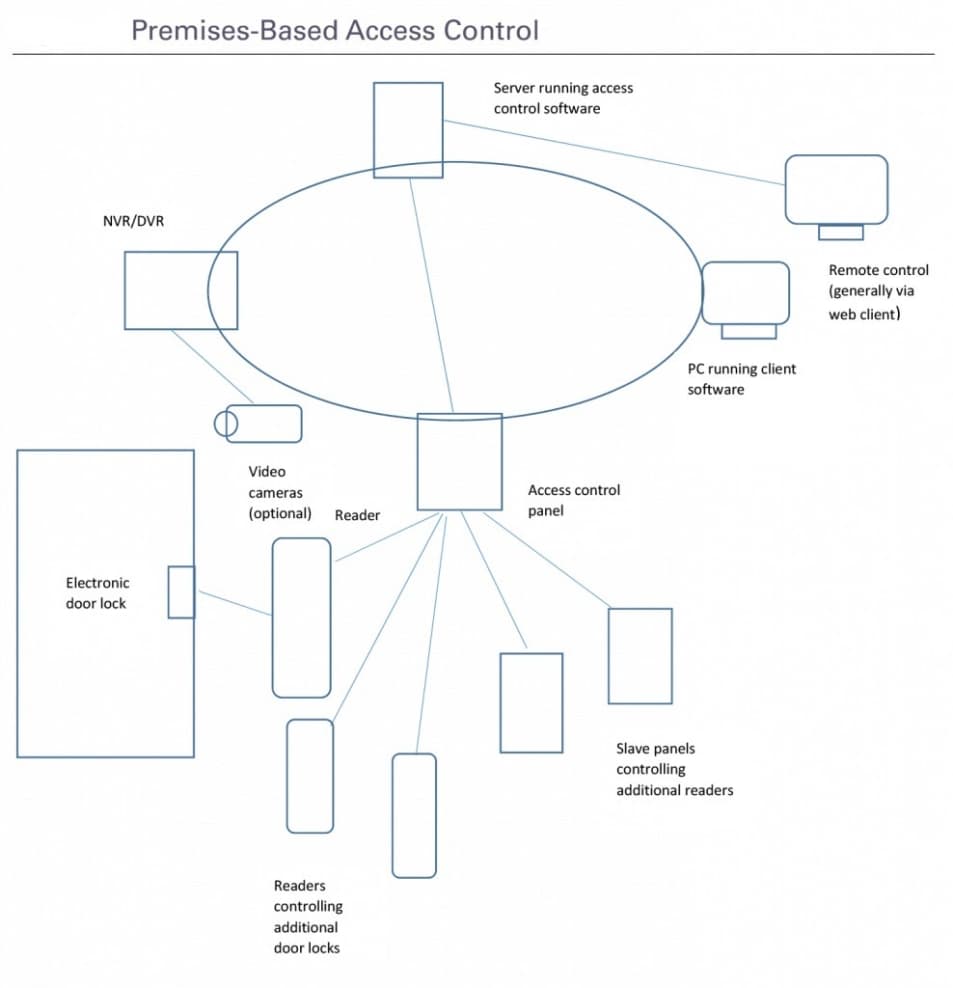
In an on-premise web-based access control system, you have a single screen or panel from which you view and manage alarms, video surveillance, facility maps, and identities.
You can also view and manage photos and employee details of your personnel. Thus, you can restrict certain employees and/or visitors from sensitive areas, granting access to selected persons only. You can also assign access levels to your employees and areas, granting employees access to a selection of areas using the access level system property.
These systems allow you to always know who is entering or leaving your premises, which door the person is using, and the time of entry or exit. An advanced web-based physical access control system will let you know where each visitor or employee is physically present at any moment in time, generating alerts if a visitor or worker is trying to access unauthorized areas.
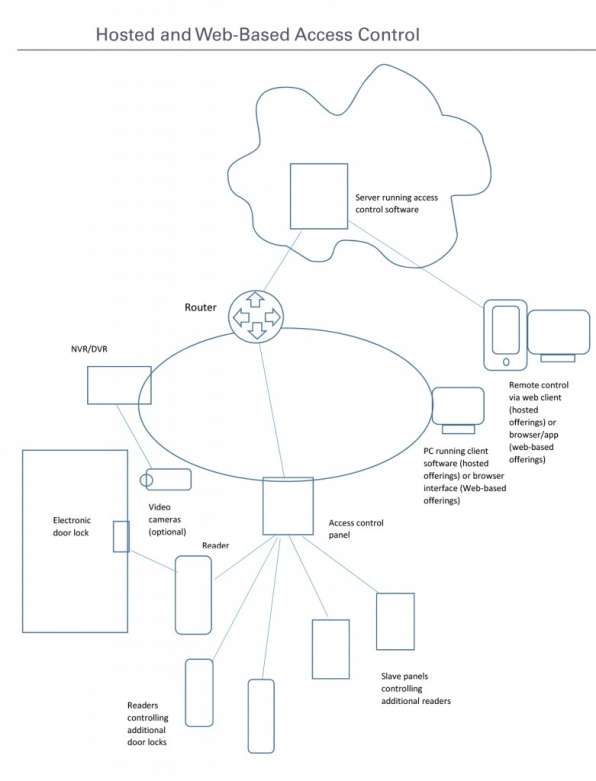
A hosted or web-based access control system is suitable for any business. This includes small and medium-sized businesses that only have a limited number of IT staff on payroll, as it only requires a little IT support and maintenance.
Cloud-based solutions are often subscription-based services and require installation only once. All you need to run a cloud-based platform for access control is an internet connection.
This type of IP-based access control system provides remote access to your control console through a secure server that can reside anywhere. The system is still operational in case of Internet shutdowns, but no software changes are available during periods of lost connectivity.
Selecting a security solution provider #
Before adopting any type of access control system, you should carefully assess your specific needs and requirements for your building’s security. Bearing in mind that security technology is advancing rapidly, as well as the methods that can be used to bypass your safety measures, you’ll likely want to opt for an access control company that offers multiple forms of authentication. These are mobile credentials, physical credentials such as cards or key fobs, a password or PIN, and biometric security that may include fingerprint or retina scanning.
Consider implementing additional security measures, such as intrusion detection, to prevent and mitigate attempts to breach the physical perimeter of your secured spaces. For instance, Kisi's intrusion detection will monitor, register and inform the alert subscriber about policy violations, e.g., when a door is forced or propped open.
Security experts suggest using at least two of the above-mentioned authentication methods. Using multiple security measures provides an additional layer of security, but you will still need to review your security and access control processes and procedures on a regular basis.
You’ll also want to select a service provider that is able to physically secure your door readers and the system’s wiring. Look for a service where the readers feature additional protection, such as tamper alarms that generate alerts in case of removal or physical altering.
Why select a Kisi solution? #
Thousands of companies worldwide choose Kisi for web-based access control.
Kisi’s web-based access control solution offers the following key benefits:
- Mobile access: Unlock doors using the Kisi mobile app, device tap, or contactless waving.
- Enhanced security: Set different access privileges, monitor entry points, track entries/exits, implement 2FA and intrusion alerts.
- Global management: Efficiently manage multiple spaces and administrators remotely.
- Streamlined operations: Integrate Kisi with Microsoft Azure, Google Suite, and more workspace integrations for process optimization.
- Optimized space utilization: Monitor access events, visualize data, and optimize space usage.
Contact us to speak to one of our physical security experts about your security and access needs.

