Kisi, and most other access control systems, make a big deal of utilizing NFC technology. However, to most people, the letters NFC might as well stand for “no freaking clue.” Hopefully, by the end of this article, you’ll have a better idea of what the technology is, how it works, and specifically how access control systems leverage it in NFC readers. If you’re more interested in the specific functions for access control, feel free to scroll down a bit farther.
What is NFC technology?
NFC stands for Near-Field Communication, and that’s essentially what it is: A method that devices have for communicating with each other when in close proximity to one another. Here’s the simplest schematic of how NFC works:
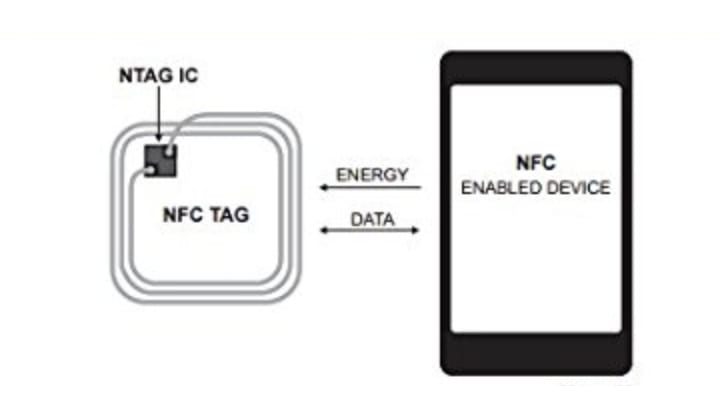
Rough schematic of NFC communication—we’ll explain how it works in the article below.
Before we get into the details, here’s some context, on the history of NFC, that might help.
Origins of NFC
The technology originated as an offshoot of RFID tech, or radio frequency identification, with the added rule that the devices had to be close to each other physically. Both techs rely on the physics of electromagnetic radio fields to transmit parcels of data. The term “radio wave” is used to denote a certain swath of wavelengths of light, and it’s used in most modern technologies as a means of communication because it can easily go through walls and generally not be hampered by physical obstacles (as opposed to, say, visible light).
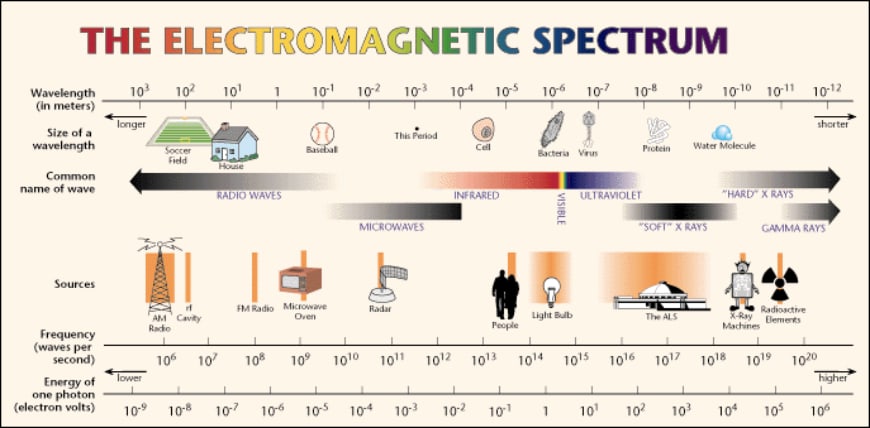
Light, as we learned in those long physics classes in high school, is a bunch of photons (that generally act like particles but sometimes display wave-like features… but let’s not get into that here!). Smart people discovered how to make those photons transmit information in the form of sequences of 1s and 0s, and we even have a language for processing those 1s and 0s: Binary code.
NFC Standards
We’ve set standards to define which sequences represent which ASCII characters—so devices, like smartphones and door readers, can send sequences of 1s and 0s to each other and recognize their unique codes—thereby achieving communication.
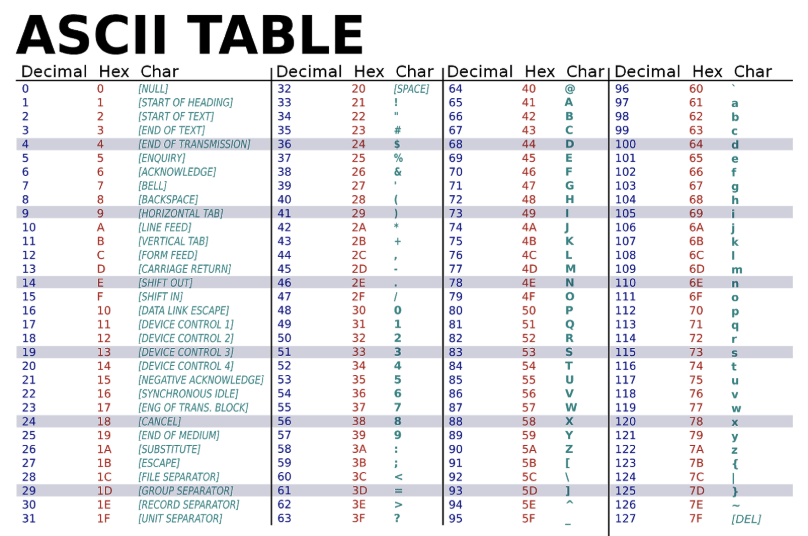
This is the science behind NFC communication.
How do NFC readers work?
So, what happens when you hold a NFC card on a door reader?

The door reader activates and transmits radio waves to induce electric current in the NFC card; passive devices don’t actually need any power source, but instead are built to activate and begin transmitting their NFC signal when exposed to a changing magnetic field.
The active devices will have an electric current running through them and, when they are put in close proximity to a passive device, they will prompt it to begin transmitting—read the signal—then the passive device will stop transmitting when it’s moved farther away.
Here’s a diagram explaining how the induced current works. The active device (right: “Reader”) has its magnetic field interact with the passive device (left: “Smartphone”) and creates a matching current to power it.

Different Types of NFC ID
The NFC reader induces a magnetic current in the token and, in turn, the token transmits the relevant string of characters. Depending on what type of token it is, the nature of this string will change: If it’s a simple ID reader, then the string is a unique identifier for the user; if it’s a transit card then it’s an ID, but on the back end the reader needs to record the charge and update its server, and if it’s a contactless payment card, then it’s an ID with many added layers of encryption and security to protect the user’s bank information (in this case, only a dedicated and approved reader could decrypt the information relevant to the bank details, any other reader would only be able to read a simple ID string).
Signal Relaying Back to the Server
After the reader reads the ID, based on the use case, the reader will then communicate this information back to the host server over local network or WiFi. Most readers only cache a small amount of information and have a method of communicating with the primary server—since storing all the relevant user info on a reader would be impractical, insecure, and would result in too bulky a product. The server will then authenticate the request and prompt the reader to perform some relevant action, be it unlocking a door, communicating with a bank server, unlocking a subway turnstile, etc. This all happens behind-the-scenes and instantaneously (depending on the strength of the WiFi signal) guarantees the end user a seamless experience.
NFC vs. Bluetooth
NFC devices transmit parcels of data via radio frequencies to other NFC devices. Hang on, that phrase sounds familiar no? That’s exactly what Bluetooth has been doing for years and years. So why do we need a different standard? Why use NFC over Bluetooth? NFC actually requires very close proximity, whereas Bluetooth devices can be much farther apart (Bluetooth can be accurate up to dozens of feet away depending on the strength of the signal) and Bluetooth devices can transmit much larger packets of data—in the megabyte range rather than the kilobyte range for NFC.
The main advantage that NFC has over Bluetooth, though—and the reason why it only works in close proximity—is that NFC devices are split up into active and passive devices, whereas all Bluetooth devices are necessarily active.
No Power Needed
The first main advantage of NFC is that passive devices, as described above, don’t actually need any power source—this makes carrying and using NFC tokens much easier. Imagine if you had to charge all of your keycards every day. That would be an incredible hassle! Instead, clever engineering makes it so the active devices (e.g. door readers) does the task of inducing the current, and the NFC tokens (e.g. access cards) can be mere passive groupings of wires and circuits that just emit a signal when prompted to do so. This relates to the second advantage that NFC devices have: Speed of communication.
Speed of Communication
Given that NFC technology assumes that the devices are in very close proximity to each other, the connection is established much more rapidly and the data packets can be transmitted more quickly. As previously mentioned, the data packets are smaller than Bluetooth ones, but for the vast majority of applications of NFC, the size is more than sufficient. All common applications, including access tokens, contactless payment, and transit cards, are merely transmitting strings of plain-text characters, which requires very small amounts of bytes (units of memory). A by-product of these engineering differences is that even the active readers require less power. They need to transmit at much smaller ranges and don’t need to transmit large data packets, so they consume energy at a lower rate. For sensors with a direct power line, this is not an issue (the financial difference is minimal), but for battery-operated sensors it can mean the difference between replacing batteries once a month and once a year.
Kisi’s NFC reader
Kisi’s own solution incorporates all the aspects that we’ve touched on here. Kisi manufactures smart door readers that are equipped with NFC (and Bluetooth) antennas. The primary unlock method, endorsed by Kisi, is using your smartphone. With Kisi’s iOS and web apps, you can turn your smartphone into a credential card—eliminating the need for any extra cards in your wallet.

The smartphone solution works because all modern phones have an NFC chip like the ones found in NFC cards and tokens. Unfortunately, Apple is proprietary about who can gain access to the NFC chip, meaning that iPhones rely on Bluetooth to communicate with the readers, but Android phones will use their built-in NFC chip to communicate with Kisi readers.
For those clients who choose the legacy card route, we manufacture and ship standard NFC tokens, both in card and fob form. These are operated by NFC technology and don’t require power; the tokens can operate continuously and at high speeds.
Learn more about NFC readers and access control
Download our physical security guide.
Limitations of NFC
Metal Interference
We’ve mentioned before that NFC reader use radio waves, which can more easily travel through solid obstacles than visual light, but that doesn’t mean that NFC communication is immune to all varieties of signal interference. Bodies of metal near any electrical signal are capable of distorting it and generally making communication more complicated and noisy.
You may have, for example, noticed that your contactless payment cards can’t scan if you don’t take them out of your wallet, or your door access cards won’t work accurately if they are bunched up with other NFC-enabled (or other metal-containing) cards. This is because the metal in other other cards is interfering with the signal from the active device (reader), and making it more difficult for the relevant NFC chip to have a current induced.
In a passive device, the NFC chip itself has two components: a coil of metal where the induced current can run and a small printed circuit board (PCB) that transmits the information. The magnetic field attempts to find the passive coil when the passive reader is presented to an active reader, and the magnetic field runs a current; however, if the chip is in active contact, or near to another body of metal (like another NFC-enabled card, or the exposed back of a smartphone), this will interfere with the signal and not allow the current to be induced.
This is why you often see NFC fobs encased in rubber and so are Kisi’s—this prevents any sort of signal interference.
Distance
As the name suggests, near-field communication requires just that—a “near field.” This means that if you try to use an NFC reader when your chip is out of range it won’t work. You may have experienced this if your hands were full and you were trying to hoist your pocket up to the level of the reader and were just too low, or, even more annoyingly, if your wallet was in your backpack and you tried to hoist your backpack up to the reader to save the hassle of fishing the wallet out.
Unfortunately, the nature of the tech means that it’s incredibly limited, distance wise, especially if there are interferences/obstacles in the reader’s way. In an ideal world, according to the NFC standards, the maximum range is about 20 cm (around nine inches), but in practice it’s often much less than that, usually maxing out around four cm.
In addition, many companies specifically limit the range of their readers to prevent eavesdropping. The applications that require secure data transfers, like contactless payment cards, have encryption systems in place over the connection; however, the less secure ones—like simple access control readers— generally don’t bother with these, so they’re vulnerable to malicious third parties reading the signal. Through limiting the signal distance to a couple of inches, an eavesdropping machine would need to be within two inches of the reader at the time that the connection is established in order to steal your data.
Speed of Secure Connections
You may have noted that there are times when the NFC connection on your contactless bank card works less than instantaneously (it takes longer than you’d like to go through). That’s because a greater amount of data needs to be transferred—the base data (card ID) is encrypted and, in practice, this means that the actual bit string communicated is much longer (and the reader will decrypt this and reduce it back to original size).
As we touched on in the NFC versus Bluetooth section, NFC data transfers are smaller in size than Bluetooth, so generally this transfer of encrypted data will take more time than it would if it were unencrypted. Kisi’s own opinion, though, is that this is a small enough price to pay for securing your data against eavesdropping!
Compatibility
Most modern smartphones have an NFC chip. However, it’s up to the manufacturer of the smartphone whether to make that chip accessible to third-party developers or not. Apple, in its fashion, has restricted access to the chip that, at its inception, only worked with Apple pay. Now, whether this was for security reasons for payment encryption or a plan to make the functionality more exclusive, is something you’ll have to ask Tim Cook. Recently, it seems they’ve been relenting, as they allowed a handful of university cards access to the NFC chip, but whether this is a one-off publicity stunt or symptomatic of a greater relaxation in their regulation is still up for speculation.
In the meantime, though, users who are gung-ho about NFC functionality will have to content themselves with an Android phone (not that it’s such a big sacrifice to make).
How to Manage Your NFC Tokens
An NFC reader, like the Kisi Reader Pro as described, is an active NFC device, meaning that it’s capable of inducing a magnetic current in a passive device, prompting it to broadcast its NFC ID. To manage those NFC tokens there will be a web app interface such as Kisi app cloud dashboard. It looks something like this:

In the example here you can assign a Kisi card by inputting its assigned token or unique NFC ID. In case you use third party cards, the NFC ID might not be immediately evident. But don’t worry,t can be easily discovered and assigned. All you’ll need is an Android phone. With this capability, you’ll be able to not only provision Kisi cards, but also any third-party card with a built-in NFC chip. This extends to a wide range of contactless bank cards and modern transit cards.
Main Takeaways
NFC technology, at its current stage, represents a significant feat of engineering. It’s possible to transmit data at close distances, and faster than ever before, using clever physics tricks and modern technologies. In turn, NFC has revolutionized the field of modern access control, as users can more seamlessly authenticate themselves with modern readers. If you’d like to give Kisi’s cutting-edge solution a try, get in touch!
Save time. Enhance security.
Modernize your access control with remote management and useful integrations.
Continue learning

