With the increasing popularity of cloud-based applications, and the power and versatility of modern smartphones, more and more access control companies are moving toward a mobile-first model. With this new standard, you’d be able to use your phone as an access card, and unlock doors with the phone itself.
How do phones manage to unlock doors?
Let’s first take a look at the tech behind mobile-based access control. Mobile-based access control relies on a couple of different technologies: RFID and Bluetooth. Specifically, many phones use the NFC standard of RFID and the BLE standard of Bluetooth for such unlocks. Both work without needing to pair the phone to the reader, meaning that you can just start using your phones as an access card with minimal onboarding! The following section will discuss these two methods and how they function.
Phones as RFID Cards
We’ve covered RFID technology at length in another article, it’s just important to remember that that RFID relies on radio waves to communicate, and the two devices in question communicate identification messages using radio waves. RFID chips exist in many variations, with the most common being NFC chips. Most modern smart access cards are NFC-enabled cards.
What’s interesting, though, is that this tech is not limited to access cards and readers: Most modern smartphones have an RFID chip inside them. Moreover, this RFID chip adheres to the NFC standard, meaning that all smartphones these days can operate as NFC cards. NFC, meaning near-field communication, is a set of regulations built over RFID tech and essentially it makes the communication quicker and more secure, while limiting it to very short distances (<1 inch) for safety and ease of communication purposes.
RFID / NFC for iOS
You may have seen this tech at play in Apple’s new Apple Pay functionality—Apple has enabled its wallet feature to access the NFC chip and approved banks can enroll cards in the wallet.

However, they are proprietary with the technology, so third-party applications cannot access the chip yet. This leaves Android devices as the primary vehicle for using NFC for access control.
NFC for Android
Android devices allow developers much more freedom with the chips, so access control apps (like Kisi) can link to the NFC chip, and have it transmit identification information to the reader when in range.
The way this works is straightforward: The reader will prompt any NFC-enabled device in range to transmit an NFC message, so when the Android phone in question is approached, the Kisi (or other access control) app will be activated, and broadcast the unique NFC code of that phone. If the user has been approved on the back-end as having access to that door at that time, then the reader will unlock. As simple as that!
Phones as Bluetooth Tags
The other primary tech that allows smartphones to interact with access control readers is Bluetooth. For a more in-depth dive into Bluetooth technology, please reference this article on the subject. Much like RFID, every modern smartphone has a Bluetooth chip installed. These are small and unobtrusive, and add so much functionality to the phone that it’s really a no-brainer to include them.
As referenced in the linked article, smartphones use the Bluetooth Low Energy protocol that, as the name suggests, uses much less energy than normal Bluetooth (because your smartphone battery is a precious and limited resource!), plus it’s more reliable. BLE provides more than enough bandwidth for all secure communication that goes on between the phone and the reader.

Bluetooth has a longer range of communication, but most modern access control apps will deliberately limit the range of their readers, to prevent any sort of snooping on the signal, or unwanted accidental unlocks. More than that, too, some companies like Kisi are implementing AI techniques to recognize the gesture of a “tap” so that the reader will only unlock when the user intends it to. Science is amazing!
Alternate Methods - QR Codes as Access Tags
Beyond RFID and Bluetooth chips, some access control apps will leverage your smartphone’s screen itself as an access method: I’m talking here about the “new barcode”—QR codes.

Each QR code is totally unique and can be displayed on any screen. If you just install a camera in your door reader, you can have it scan a unique, one-time or permanent QR code from a user’s smartphone screen, and use that to read authentication and identification information.
Of course, the inherent risk with this is that users will print their QR codes, or take a screenshot of them and share them, rendering the door less secure. It’s much easier to share a screenshot than your phone itself.
This doesn’t mean that QR codes are hopeless, though—they’re quite useful in fields like visitor management, where a one-time password needs to be shared in an easy-to-use way. The QR code will only work one time, so sharing isn’t an issue and the visitor doesn’t need to download any new app on their phone—they can simply open up an email or text with the code inside it.
Door Lock Apps: Advantages Over Access Cards
Smartphones, by and large, use the same tech as access cards to communicate with readers. So why use them instead of access cards? What are the advantages of mobile access credentials?
Onboarding and Offboarding
Ease of Manual Onboarding
Cards are a hassle! We all have tons of them lying around, in various states of disuse, and if you’ve ever been in charge of onboarding and offboarding new members into your office, and passing out or picking up access cards, you’re all too familiar with the excuses and pleas for a new card because they lost theirs.
Thankfully mobile access solutions simplify this process. Mobile access control solutions will have some version of an admin dashboard for their app and, through this dashboard, you can very easily add and remove members—so long as they’ve created an account on the relevant app.
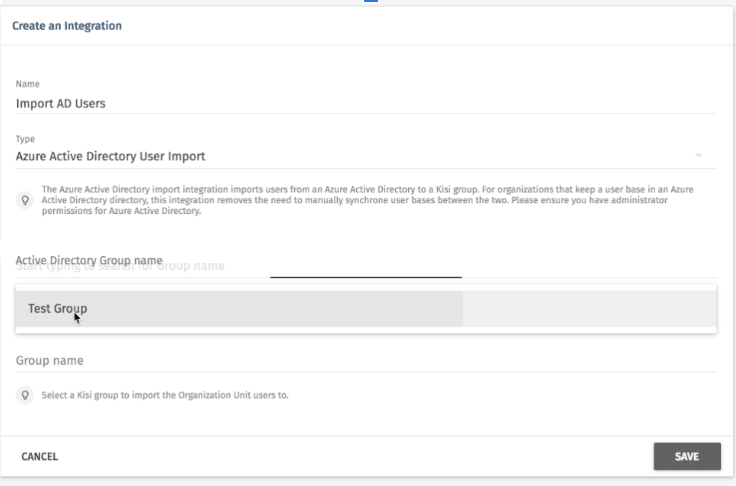
Automated Onboarding
Many modern apps have integrations with active directories like Microsoft Azure or Google AD. With these, you can automatically import and onboard whole groups at a time so you can focus on your business rather than having to go through this hassle yourself.
Reduced Risk of Lost Cards or Shared Cards
People lose their cards. It happens. It’s just a hunk of plastic and if you lose it no big deal, the IT admin will just happily hand over another one, no harm done right?
Wrong! Not only is this a huge hassle for any admin handing out cards, it’s also a serious security issue. Unless the admin has been keeping good logs, it’s sometimes difficult to keep track of who was using which card, and even then, a user might not report it for embarrassment or fear of punishment. At that point, you have an active card floating around somewhere and, very realistically, somebody could pick it up and gain access to your space.
With a mobile solution, though, there is a much smaller risk of this happening. People are less likely to forget, misplace, or share their phone than a random access card. Just think about how you treat your smartphone and how much you’d freak out if you lost it.
Interactive User Interface
Finally, mobile-based access apps have a nicer user interface and user experience than card-based access systems. You can easily track your usage, view all your locks, and use the mobile app as a sort of backup in case BLE/NFC are malfunctioning.

This also makes error reporting much easier—instead of having to message the IT admin on a separate platform and risk it getting lost in the noise, or forgetting to go check in, odds are that your mobile solution will have an established flow for reporting errors and even a section with solutions to common errors.
Advantages of Cloud-Based Systems
Arguably one of the biggest advantages of a mobile-based access system is that is allows you to fully leverage the capabilities of a cloud-based system. Cloud-based systems don’t necessarily require a mobile solution; as long as the reader is networked to the access company’s servers, the company can use the cloud. However, mobile solutions use cloud tools to the fullest.
Cloud-based systems store all their data on decentralized servers, meaning the access control company holds the data, saving the end user from the hassle of having to keep servers and perform maintenance. Let’s now look into some ways that mobile apps leverage cloud capabilities.
Data Tracking
A big advantage of a cloud-based system is that the access company will often do data tracking and analysis for you, allowing you to glean insight into the usage of your rooms and time of unlocks, among other information.

Mobile solutions increase the reliability of these systems. For starters, you can feel confident that the people you are monitoring are actually doing the unlocks themselves, rather than sharing their cards. On top of that, you can actually have access to data from the smartphone itself, like location services to see if the range is functioning properly, or error reporting if something went wrong with the phone’s bluetooth/NFC chip rather than the reader’s system.
Notifications and Messaging
Independent of data tracking, companies often want their users to get notifications related to their access control.
With a legacy card solution, this process is a bit more complicated. IT admins will have to message users separately on another platform, which decreases the probability that the message gets seen and gets resolved; however, with a mobile access solution it’s really a no-brainer: You can just send a notification through the app for whatever change or message you want to send to all end users.
Security Protocol Enabling
Beyond simply onboarding users, sometimes the access control company will detect some security breach or flaw in the system and want to implement emergency security protocols. With a card-based solution, this is very difficult, as you’d have to get the message out to all users, informing them of the change in protocol.
However, with a mobile-based access control solution, the admin or access control company can automatically implement the changes directly on the user’s phone apps and change security authorizations, or any other relevant features, in order to address the issue.
Concluding Thoughts
Card-based access control systems have been around for a while now and certainly present many improvements on old-fashioned lock and key systems. However, they should watch their backs, because there’s a new player in the game: Mobile-based access control apps.
Mobile solutions present many advantages over older systems, and with the huge surge in popularity of cloud-based systems and mobile apps, it looks like they’re here to stay. Make the switch today.
Save time. Enhance security.
Modernize your access control with remote management and useful integrations.
Continue learning

