If you’ve been working out of tech offices or coworking spaces for a while, and have bounced around companies a bit, chances are that your wallet is by now chock full of different kinds of access cards used to get into various offices and conference rooms. As you now check your pockets and contemplate which to throw out and which to keep “just in case,” you may be asking yourself what the difference is between all these cards. Don’t they all have the same tech? Shouldn’t you be able to reuse them from one office to another, by just reprogramming them? In this article, we’ll cover some of the main protocols used in access cards, the advantages and disadvantages of them, and our own recommendations.
The Tech Behind Access Cards
Before we dive into the different varieties of cards out there, we should discuss what the tech is behind access cards — how do they actually communicate with the smart readers you have at your doors? We’ll review the science of RFID, and move on to the NFC standard, which adds some regulations and makes the technology more secure!
RFID Protocol
Every smart access card you have is built on what is known as radio frequency identification, or RFID for short. Basically, RFID is the function that allows devices to communicate with each other via radio waves, using them to transmit information back and forth. This information mainly extends to self-identification: the devices transmit unique identification tags that other device recognize, and then are used to run authentication algorithms.
One of the most clever innovations of RFID is its ability to communicate with chips and distinguish between active and passive devices. Both devices have RFID tags that are essentially loops of wire with chips attached, and the chips contain the sophisticated circuitry that communicates the data.
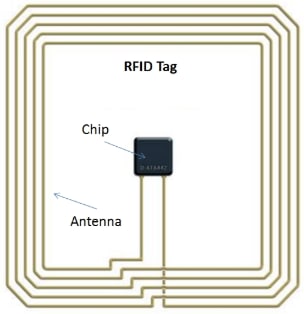
However, the greatest innovation is that the passive device doesn’t actually need a continuous power source. It can remain inactive most of the time, and when it approaches an active device, the active device will induce a current through it. This means that the passive device can be anything from a key fob to a smart card, without needing batteries or charging.
The range of an RFID object can theoretically extend to an unlimited distance, depending on the strength of the active device, but in practice most active devices keep their range low, with a radius of only about a few feet, both for safety reasons (to prevent eavesdropping) and to conserve power (it would need to be massively powered to transmit over long distances).
NFC Standards
The NFC (near-field communication) standard was introduced in 2003 as an improvement on RFID technology. It allows for more secure and speedier communication over short distances using a specific band of radio waves within the range of RFID. For a more complete overview and deep dive into the NFC standard for cards, take a look at this article!
The takeaways here are that NFC is highly secure and encrypted, with many layers of security inherent in it. Even if all you are transmitting is the NFC ID, with any application this ID will be encrypted and protected against any sort of malicious theft attempt. NFC also works very well over short distances, transmitting small (yet still sufficiently large) data packets between a passive device (like a card or fob) and an active device (like a reader or smartphone). To tell if your card is an NFC card, you merely need to look for the NFC signal on it, which looks like this:

NFC and RFID Card Types
General RFID cards, and more particularly NFC cards are used very commonly in access control and mobile payment, the latter primarily in transit cards and bank cards. In this section, we’ll review how those work, and which cards you might find yourself using.
Access Cards
One of the primary purposes of NFC and RFID cards (arguably the most important, in our opinion!) is access control. Indeed, thanks to the unique nature of the RFID tag in these cards, they can be assigned to any given end user, and then when that card is tapped to the reader, the reader recognizes the signal and authenticates based on whether the user is authorized to use that door.
Now, clearly, there are many different kinds of access cards. They come in many shapes and sizes, and different companies impose different restrictions on their use. Considering this you may be wondering what kind of card you have and whether it is secure. As a general rule, if your card is an NFC card, then it will have a secure communication protocol enabled. Refer back to the NFC article for an explanation of this. As an example, here is an action shot of Kisi’s NFC card in use!

While RFID is a general protocol about sharing information over certain radio frequencies, the NFC standard is a set of strict rules that all NFC cards have to follow, and that includes security, and strength of the connection.
Many access control systems, like HID (more on HID in a later section), only allow you to use their proprietary access cards to function with their readers. While this does allow for more control on the part of the admin and the company itself, it means that you might accumulate a bunch of mutually incompatible cards in your wallet. More modern and future-proof solutions, like Kisi’s reader, will allow you to enroll whichever NFC card you already have to unlock the readers.
While Kisi manufactures and sells our own NFC access cards, you also have the option of enrolling whatever legacy card you are already using into Kisi’s system. For more details on this feature, visit this link. You can also find a screenshot of the Kisi dashboard, where you can assign and unassign any NFC token or card that you already have at your disposal.

Smartphones as Access Cards
As you may have guessed reading up to this point, NFC and RFID (and even Bluetooth) tags are so versatile and small that they are installed in every modern smartphone as well. As a result, many modern access control companies like Kisi are leveraging these capabilities to allow you to use your phone as an access card for entering a building.
In Kisi’s opinion, this presents the final solution to eliminating unnecessary plastic from your wallet, and to securing your data. Smartphones can allow themselves to have far more heightened security and encryption protocols, as they are not as limited in size as access cards or fobs. Also, as every article on the web never fails to mention, millennials are addicted to their phones, so it’s unlikely that you’ll forget it at home.
HID cards
We will take a brief detour now to talk about HID cards. HID is a company, not a standard or category of cards, so if you have an HID reader on your doors, you will have an HID card to unlock it. HID cards are generally quite secure and have many fail-safes. For a more in-depth look at different kinds of HID cards, and to review which you might have, take a look at this article on the Kisi blog.

Transit Cards
Another place you may have seen or used a contactless card is in modern transit cards. Many cities are moving away from the clunky and unreliable old daily paper passes, or swipe cards, and moving towards more modern contactless solutions. As is usually the case with these modern contactless innovations, these cards use the NFC protocol. You’ll notice your card is NFC because it has the NFC logo, as referenced above, on it. A relevant example of such a card would be San Francisco’s Clipper Card.

Contactless Bank Cards
One of the latest inductees into the world of contactless tech has been the banking industry. Many banks have aren moving towards NFC technology given its safety and ease of use, and have inserted NFC tags into their bank cards. These cards are incredibly safe, and difficult to hack, and allow you to pay without having to go through the annoying and unreliable chip reader or swipe method.

Transit and Bank Cards in Access Control
If clients already have these perfectly usable NFC cards in their wallet, like modern transit or contactless bank cards, why make them get a new card and clutter their wallet?
This is the dilemma that modern, adaptable access control companies like Kisi are trying to solve. In the mission to make access control as painless and safe as possible, why not leverage the security and ease of use of existing NFC cards, and allow users to enroll those cards to unlock door readers?
With new integrations and the versatility of Android phones, Kisi has actually enabled this feature. We’ve introduced a new flow in the Android app that allows you to “read” your NFC card from your phone, decode the NFC ID, and enroll that to your Kisi account.
Concluding Thoughts
With so many different kinds of access cards out there, it can be difficult to know which one you have, or whether yours is secure, or even if you need it anymore. Hopefully, this article has cleared up some of those uncertainties for you, and convinced you that maybe access cards are a thing of the past, in a world where mobile is the new king!
Save time. Enhance security.
Modernize your access control with remote management and useful integrations.
Continue learning

