Workplace security is critical to any organization’s success—it directly affects productivity, employee morale, and financial performance. In a 2022 study, 97% of workers said feeling safe is an important consideration when deciding where to work, and 58% said they would begin looking for another job if their employer failed to communicate effectively about an emergency or dangerous event.
The question for most companies is how to create the secure office environment employees, customers, visitors, and other stakeholders need and deserve. In this guide, we’ve put together a list of the top security tips for the workplace so you can make that safe atmosphere a reality.

1. Use mobile access control #
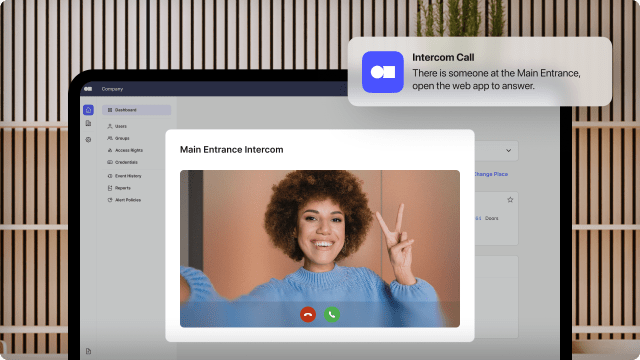
An access control system is the heart of any work security strategy, and mobile credentials and management have made it more efficient and convenient than ever. Mobile access creates a better experience for administrators and users alike, allowing you to control the system remotely and unlock doors with a smartphone, smartwatch, or CarPlay.
When you use a cloud-based access control solution with a mobile app, you can grant or revoke access credentials when not on the premises simply by logging into the system. You can also initiate a manual lockdown if a security incident occurs and receive alerts about attempted intrusions.
Employees and authorized guests can use their devices to unlock doors. Depending on what kinds of credentials you choose, they can tap a button in the mobile app, hold their device close to the door to trigger the unlock, or wave their hand in front of the access reader. These options are significantly faster and easier than digging out a key or making sure you always have a key card or fob on hand.
2. Implement time-based credentials #
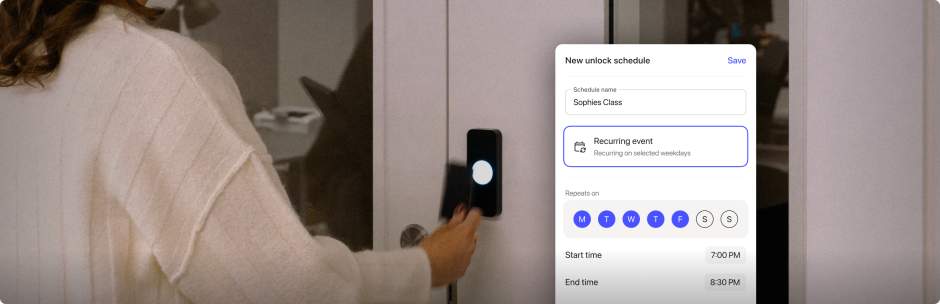
Another way to enhance your access control system is to take advantage of its scheduling capabilities. With solutions like Kisi, you can set recurring or one-time unlock and access schedules. This means you can not only control who enters your space but also what days and times they have access.
When using time-based credentials, you can set up a single event to unlock the doors for a specific window or all day. For example, if your organization is hosting a conference or event, you can create a schedule so the doors remain unlocked throughout the day so guests can enter without assistance from staff.
Alternatively, you can establish a recurring event, leaving doors unlocked at specific times for certain days, such as your days of operation. For instance, if you regularly welcome customers or clients onto the premises, you might opt to set the doors to unlock at the beginning of the workday and lock at the end of the day. With this approach, you don’t have to worry about employees forgetting to lock the building before they leave. To ensure the building is secure at all times, you can make exceptions for holidays or special circumstances when your business will be closed during regular operating hours.
3. Grant role-based access #
Security in the workplace involves determining and managing who can access specific doors and areas of the building. An effective access control system allows you to assign users to roles with different permissions at the organization, group, or place level.
This is especially important for organizations handling sensitive information. In many cases, only individuals with the appropriate training and clearance have permission to read and share confidential documents. Failing to prevent unauthorized workers, customers, or guests from accessing these files could result in a significant compliance violation and put the privacy of your employees and clients at risk.
With role-based access, you can restrict entries to off-limits spaces based on each person’s role. For example, you might give administrators access to all doors but prevent other employees from entering document storage areas. Similarly, if you operate a business with regular customer traffic, you can use role-based access to separate employee-only areas.
4. Train employees on tailgating #
One of the best ways to make your organization safer is to ensure your employees have workplace security awareness. Along with teaching them about fire hazards, emergency procedures, and lockdown processes, your training should also address tailgating.
Tailgating occurs when an unauthorized individual tries to enter a space by closely following someone who has scanned their valid access credentials. These incidents aren’t always malicious—sometimes other employees don’t want to bother pulling out their own credentials. However, they make your organization vulnerable to potential criminal activity, including theft and data breaches.
When developing your security training program, include a section on how to properly use credentials and emphasize that employees should never hold doors open for others, even their coworkers. Explain why tailgating is a risk, and give detailed instructions on what your team should do if someone tries to follow them into the building.

5. Modernize your visitor management #
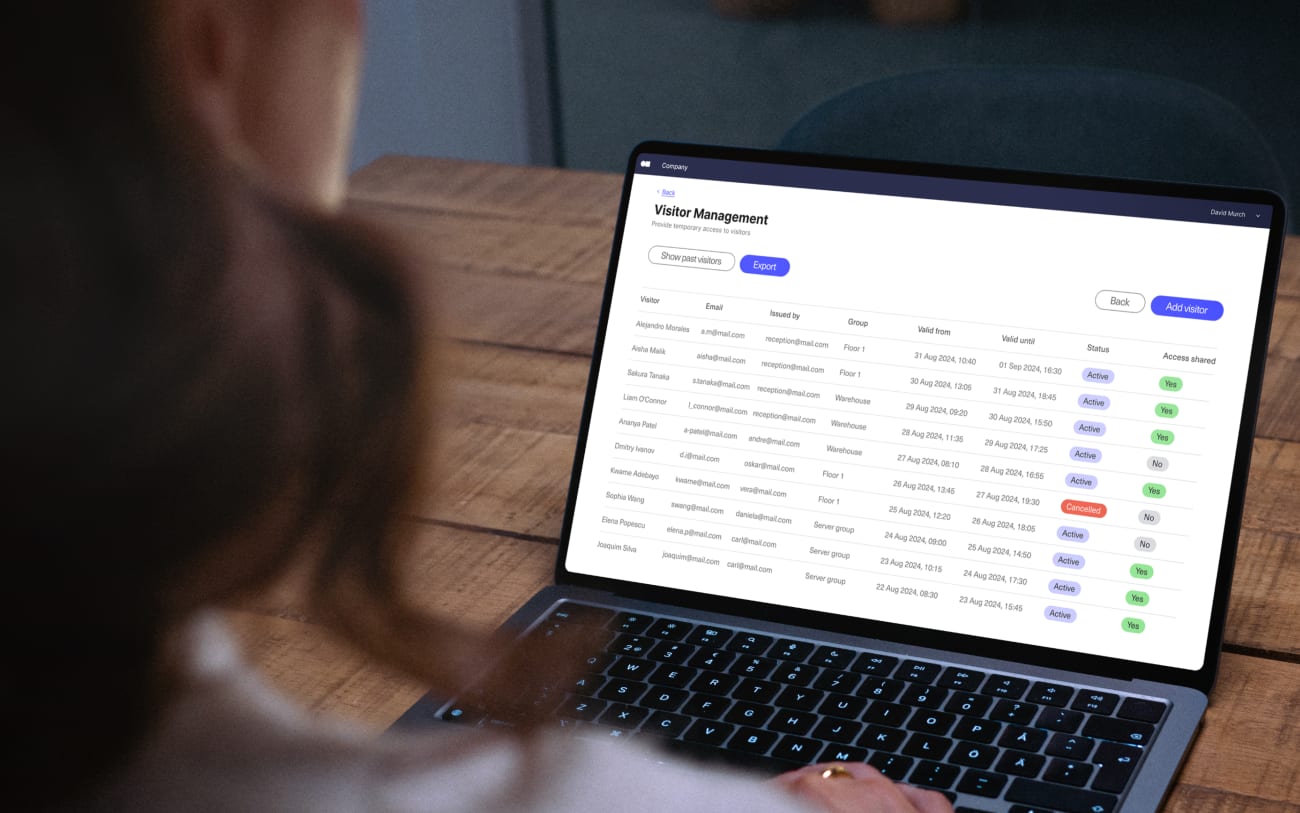
If you’re still using paper logs and sign-in sheets to track visitors, a digital system is a major upgrade that will pay off in significant ways. Some modern solutions, like Kisi, even include digital logs as part of their free plan. A tablet kiosk system is an especially good option because it’s a space-saving solution with low power consumption.
Implementing a visitor management system allows you to see how many people and who exactly is on site at all times. This information is critical if you need to evacuate or investigate a security incident. It also increases visitor privacy and makes it easier to verify visitor identities, particularly if the system can scan driver’s licenses or other forms of identification.
6. Pre-register visitors #
Another benefit of an updated visitor management system like Kisi’s is the ability to register visitors in advance. Enabling visitor registration before guests arrive at your site means you can streamline check-ins, so you’re less likely to have crowds forming in lobbies or reception areas.
Pre-registration also means you can check visitors’ names against lists of banned or high-risk individuals before they even arrive at your building and, if necessary, flag them for security. If your organization requires guests to sign non-disclosure agreements (NDAs) or other documents, they can take the time to review all the details and fill them out ahead of time.
7. Audit visitor logs #
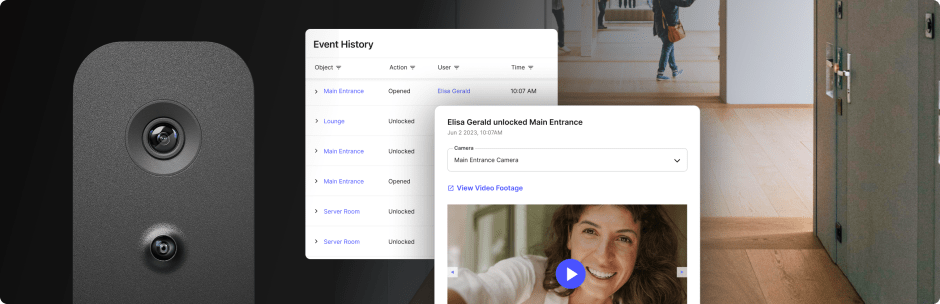
The visitor logs you generate with your management system can give you valuable insights into weak points of your security system, but only if you periodically review them. An audit helps you better understand traffic patterns, including when volume is higher, so you can plan accordingly for staffing and security personnel. It also allows you to identify specific individuals who are exhibiting unusual behaviors, such as a sudden uptick in unexplained visits.
Audits are critical when it comes to compliance. They can help demonstrate you’re meeting the requirements regulators set for safety or data privacy. You can also use them when investigating security incidents, particularly if you can tie a pattern of theft or property damage to repeated visits by certain individuals.
8. Install extra sensors and alarms #
When an emergency breaks out at your business, responding quickly can protect human health and limit the extent of the damage to your property. Many organizations already have the basic alarms in place for natural threats, such as:
- Fire alarms
- Flame detectors
- Heat detectors
- Carbon monoxide detectors
- Smoke detectors
However, today’s alarms and sensors cover a lot more than just the threat of fire or gas leaks. For example, Kisi’s access control system offers intrusion alerts to let you know right away if someone enters your property without authorization. Many businesses use broken window sensors, which trigger security alarms. You can also use motion detectors to activate lighting, which can be enough to frighten away thieves or intruders.

9. Automate key security processes #
Whether you operate a small business or a multi-site enterprise, managing security in an office setting is a lot of work. Automation can alleviate much of that burden and make your property more secure at the same time.
In addition to automating your access control and alarms, consider further steps like automatic badge printing. A digital visitor management system can instantly print visitor badges when they check in to your building, saving time for your employees and ensuring everyone on-site is clearly identified.
Another area where automation is making a major impact is video surveillance and threat detection. Advanced video analytics and facial and object recognition can pick up suspicious activity even when no one is watching.

10. Integrate security solutions #
Connecting all your security solutions creates a cohesive system with simplified management. Integrating your video surveillance, access control, and alarms with a system like Kisi’s One Security Platform means you can control everything from a centralized platform. An integrated system also reduces false alarms, speeds up response times, and allows for more effective incident detection.
In addition, you can verify information across systems in a single platform. For example, if your access control system shows an individual entered the building at a certain time, you can confirm that fact with footage from your video surveillance system. This corroboration is vital when making a case for a criminal investigation or insurance claim.
11. Store security data in the cloud #
Saving video surveillance footage, access logs, and visitor records on servers in your building used to be standard practice, but an increasing number of organizations are sending their files to the cloud. Using cloud storage protects data from theft or damage and saves space.
Cloud-based access control and video surveillance are also preferable to on-premises legacy systems because you can access the information you need at any time, no matter your location, and act upon it remotely. If you need to verify when an individual last used their access credentials, for example, you can get online and check the logs through the cloud and decide whether to remove their access privileges instantly. The constant accessibility and remote control are key to staying fully informed and vigilant about the security at your building.

12. Develop clear policies #
We’ll finish this list with a basic but incredibly important step: Writing a comprehensive, detailed policy. All the solutions you install and training you create will go to waste if you haven’t documented every element of your security strategy. Unwritten rules and vague statements can leave your team confused and cause chaos if an incident occurs.
Putting your policies in writing will increase adherence and improve your incident response. Taking a proactive approach will also reduce the number of security incidents that occur and help you maintain regulatory compliance.
If writing a set of security policies from scratch is overwhelming, don’t worry. You can start with an existing example of a security policy and adapt it to align with your organization’s unique features, strategies, and tools.
Get the best security tips and technology from Kisi #
Workplace security is a cornerstone of operational efficiency and organizational growth, not to mention employee and guest safety. Following these tips can help you optimize your strategy and create a more positive environment, but implementing multiple changes and improvements is challenging.
Partnering with Kisi can help you overcome any hurdles when updating your security approach. We’ll introduce you to our future-proof access control system and integrated security solutions.
Reach out to learn more and request a demo.

Vera Eftimovska
Marketing Campaign Manager at Kisi, blends her psychology background with hands-on experience in access control and workplace security. Passionate about how technology and human behavior intersect, she shares insights that help businesses build resilient, future-ready, and security-driven workplaces.