Striking a balance between welcoming visitors to your organization and maintaining building security is often challenging. Guests should feel comfortable and valued from the moment they enter your doors, but those priorities shouldn’t come at the expense of safety for your employees and assets. An effective visitor log system can simultaneously meet both goals.
In this guide, you’ll learn everything you need to know about visitor logs, including what they are, why they’re useful, and what they include. You’ll also get a detailed look at the different kinds of logs available and how they might align with your organization’s needs.
What is a visitor log? #
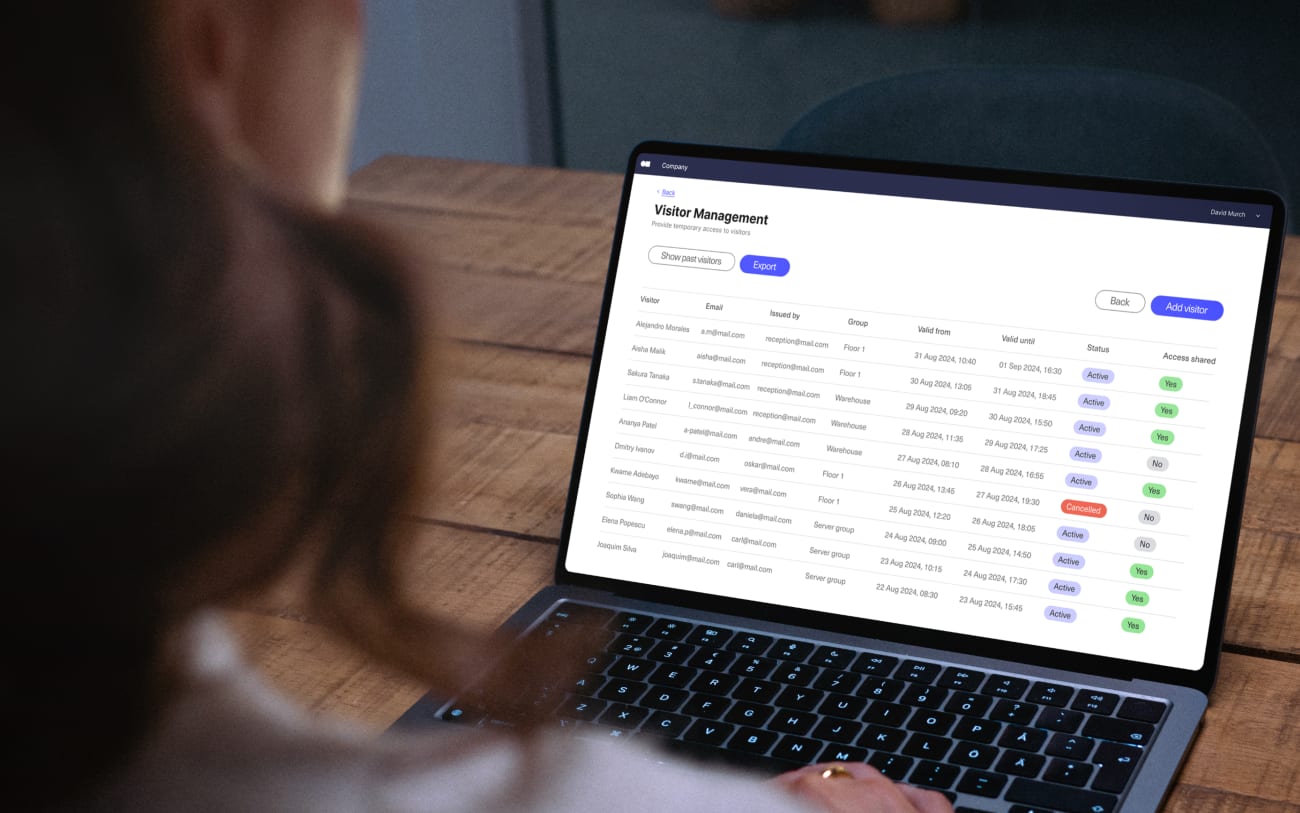
A visitor log is a record-keeping tool organizations use to keep track of the people who enter their buildings. It’s often part of a larger visitor management system and contains key details about each individual, offering greater insight into who they are, why they’re visiting, and how you can contact them.

Formats #
Visitor logs are available in two formats: traditional and digital. Traditional logs are paper-based and typically stored at the front desk, security station, or reception area of the property. When visitors arrive, they speak to a staff member or security officer and add their information to the log.
Digital logs are a more modern alternative to physical log books. Some organizations use simple computer spreadsheets, but many have made the switch to automated visitor log book software. With these systems, visitors enter their information on a computer or mobile device. The system stores their details and allows employees to access it at any time. Many digital solutions also have additional features, such as automatic notifications and photo captures.
Common information required #
Organizations collect different types of visitor information based on their security requirements and unique needs. However, these are some of the most common fields people have to complete when signing in:
- Full name
- Date
- Time of arrival
- Time of departure
- Organization they represent
- Reason for visit
- Host
Organizations with especially high security levels may also require visitors to sign additional documents before entering. For example, some businesses ask guests to sign non-disclosure agreements during the sign-in process. In these cases, the log may also include a checkbox or signature field confirming the necessary documents have been reviewed and signed.

Purpose #
Organizations using visitor logging systems are usually trying to meet several goals. First, they want to increase security by ensuring they know who’s entering the building. Requiring visitors to sign in enables you to prevent unauthorized individuals from entering.
Visitor management is also beneficial if a security incident occurs and you need information about who was on the premises at the time. In addition, it’s imperative if you have to evacuate the building during an emergency. With a log, you know who is present and can evacuate them, protecting everyone from danger.
Finally, visitor logs are useful for data analysis. By reviewing the log history, you can learn more about the visitors you’ve had, including who they are, what organizations they represent, and when they typically visit. This information helps you make more informed decisions about security and scheduling.
Visitor log types #
You can choose from a variety of solutions when implementing a visitor booking system. Each kind has advantages and drawbacks:
- Paper log books: Paper visitor logs were the most common type of logging system in the past, with organizations using binders with printed visitor sign-in sheets or spiral-bound notebooks. This is a simple, straightforward solution with no advanced features or capabilities.
- Digital logging software: A digital log allows visitors to enter their name and contact details on an electronic device to sign in. It usually also allows them to sign out, pre-register, and send notifications to the host when a visitor arrives.
- Integrated visitor management platforms: Visitor management software takes everything a digital logging solution can do and expands upon it. It typically includes not only sign-in functionality but also integration with other systems, such as access control and video surveillance, as well as more advanced security features.
The size, structure, and nature of your organization will ultimately determine which of these visitor log monitoring systems is the best fit.
Comparing manual and digital systems #
Many organizations still rely on traditional paper logs, but manual visitor logging comes with significant challenges. By contrast, digital log books offer several benefits that aren’t possible with paper-based systems.
Security #
Increasing security is a core function of tracking visitor entries and exits, but manual logs have some serious limitations. For example, they’re easy to manipulate, meaning that other visitors or staff could change or erase important information. It’s also difficult to fully restrict access to log books so they can’t be tampered with and visitor information remains safe.
Digital log books are inherently more secure because information is stored electronically. This makes it much more challenging for unauthorized individuals to view or alter it. Many digital solutions also offer extra security features, such as identity verification using ID cards.
Accuracy and data integrity #
Another difference between manual and digital logging is their accuracy. Physical visitor logs are susceptible to human error. For example, a visitor might enter incomplete information or write illegibly. This can make it difficult for staff members to verify a visitor’s identity and introduces problems if someone needs to review the log in the future.
Even storing paper log books can quickly become cumbersome and expensive. As a result, they’re generally only appropriate for small businesses with low visitor traffic.
Concerns about legibility don’t exist with digital systems because users type their information rather than writing it by hand. Digital files are less likely to be damaged or lost, so the data you store is more likely to remain intact and accessible than if you use paper logs. Scaling your data storage is also simpler because servers and cloud storage are typically less expensive and require little to no physical space.

Efficiency and cost #
Although a paper log book and pen are inexpensive, the full cost of manual logging—in terms of labor, time, and money—is much higher than many people realize. Manual logs require constant oversight and staffing to ensure they aren’t stolen or manipulated. They can also create a bottleneck when welcoming visitors to the property. A line can quickly form when every visitor has to handwrite their personal information in a single log book.
A digital solution eliminates these issues because visitors can independently complete the sign-in process. What’s more, some visitor management systems, such as Kisi, offer digital visitor logs as part of their free plan, providing extra security at no additional cost.
While advanced visitor log software might require an initial investment, most systems don’t require constant staffing to maintain security. For example, some systems feature a visitor management kiosk, which guides guests through the sign-in process. In addition, visitors can pre-register, allowing them to move through the sign-in line more quickly.
Transitioning to a digital solution #
Organizations that have become accustomed to using paper logs may find it difficult to shift to a digital approach. Before you commit to making the change, consider whether it’s necessary and how you’ll select a solution for your organization.
When to upgrade to a cloud-based platform #
If you’re wondering whether it’s time to upgrade from a spreadsheet or binder to a cloud-based platform, start by thinking about how well your existing system is working for your organization. More specifically, consider whether it’s causing issues such as:
- Long visitor wait times
- Limited data
- Staffing problems
- Security vulnerabilities
- Compliance concerns
Think realistically about how seriously these factors are affecting your organization and how upgrading your system might improve them. If you’re concerned about the financial impact of switching to a new system, look into a few potential solutions. Several options offer free or low-cost plans that are often more than sufficient for small and medium-sized businesses.
What to look for in a visitor log solution #
When examining possible software, the first step is to decide whether you want a relatively simple visitor log book system or a more advanced visitor access solution for modern workplaces. After you’ve made that decision, you can select a specific solution.
These are some of the features to focus on when evaluating your options:
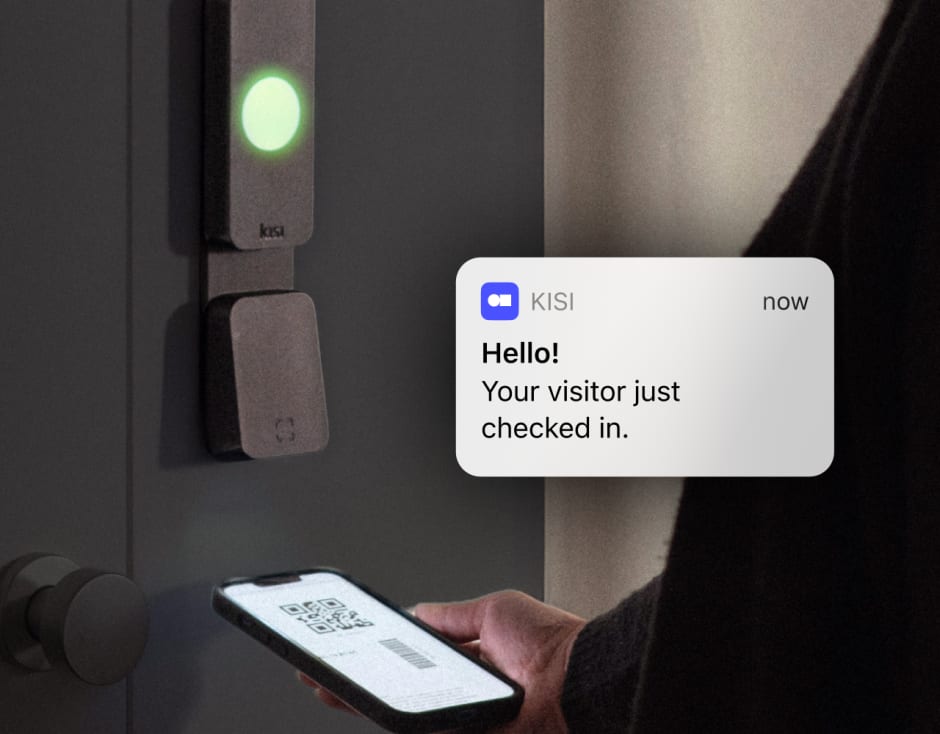
- Contactless check-in: Some systems allow visitors to pre-register and then check-in using their mobile phones or QR codes. This approach promotes visitor health by avoiding the spread of germs or bacteria and is often faster.
- Pre-registration: Pre-registration allows you to collect detailed information without contributing to long visitor wait times. It also makes check-ins more convenient for visitors by allowing them to register at the time that works best for them.
- Real-time monitoring: Digital visitor logs make you aware of who is on your organization’s property at any given time. Host notifications and sign-out requirements are an equally important component of visitor monitoring.
- Badge printing: Visitor badges make it easy for staff to recognize whether someone is authorized to be on the premises. Some solutions support this approach by automatically generating badges as visitors sign in, so guests don’t have to wait while a staff member prints a badge for them.
- Analytics: A system with reporting and analytics capabilities gives you a deeper look into visitor patterns and behavior. Look for a system that can run reports and flag trends, including how long visitors typically stay, which offices and individuals they tend to visit, and what organizations they work for.
Providers like Kisi offer a combination of all these features, as well as integrations with other essential services, such as access control and video surveillance. Kisi also offers flexibility so you can find a solution that fits your budget, including a free plan and a free trial for paid plans.