If you currently work in an older or semi-modern office, chances are you use some combination of physical keys and key cards to unlock your doors and access your space. It’s also likely that you’re often frustrated by this process: fumbling around in your pockets, backpack, or wallet, forgetting them at home or on your desk on the way to the bathroom, or maybe even losing track of them entirely. Well, the good news is that there are alternatives out there! In this article, we’ll discuss how you can avoid using key cards and keys, and explore the alternative: modern access control.
History: the Heydays of the Key and the Key Card
As much as modern access control is the future, the key and the key card have had their day in the sun, and have certainly transformed access control and served their purpose well. We’ll look at some of the history behind the key and the key card, focusing on the core features of each one.
Modularity: Multiple Passes to Open the Same Door
Maybe the most important feature of any access control system is the fact that you can have one access point with multiple people able to access it. It seems an obvious idea to anyone thinking about it these days, but it’s deceptively clever.
Many Keys Can Open the Same Lock
Imagine you are designing an access control system, without any knowledge of what keys or key cards were, and without any context whatsoever. Your first thought would be to make a one-to-one system, with some sort of lock that had its own dedicated key. That would certainly work, but the idea of making locks modular and accessible by multiple cards is a stroke of genius. This way, you can restrict access to not just one specific person, but to a wider group of people.
What if your office manager was the only one with a key to the office? You’d all have to wait for one person to unlock it every morning, and they’d have to be the last one out at night! Or if your mom was the only one with a house key. I don’t even want to think about what that would mean for the American household.
Many Key Cards Can Access the Sam Reader
This modularity of use was totally copied in the modern era with the arrival of key cards and fobs. Again, it seems obvious that many cards should be able to access the same reader, but that’s only because this functionality has been in place for millennia with regular keys.
Modern key cards take this to the next level, with their programmability. A reader is just a Bluetooth and NFC receiver, and with their Bluetooth and NFC chips, any modern card can be granted access to any modern reader that it’s compatible with. This means that you can have a single reader that’s equipped to recognize any number of cards with compatible NFC or Bluetooth chips.
Customizability: Different People have Different Access Levels
Another stroke of genius is the creation of keys: customizability, and the ability to grant different levels of access to different people, all with the same key. If you don’t immediately see where we’re going with this, think about a master key: a master key is a single key that has access to all the locks in a given space, whereas other keys might only have access to one or a few of those locks.
Keys accomplish this with a complicated system of cylinders and pins, but key cards use a more sophisticated computer science solution. Readers can be programmed to respond to and allow access to any given number of cards and to deny access to any other number of chips. Moreover, different readers controlled by the same system can be programmed differently, such that a given employee might have access to fewer doors than, say, a sysadmin.
This customizability is key to any good access control system. If you ever want to institute any sort of hierarchy in your organization, even if it’s hierarchy only in practice and not in name, you’ll want to have some sort of physical manifestation of it. Access to different areas is key to that, both as a requirement and indication of status. An admin will need more access than a common employee and will want it as a show of the increased responsibility that he/she has.
The Modern Alternative to Key Cards: Access Control
Now that we have some key components of a good access control system laid out, we can explore modern alternatives to keys and key cards, and make sure that they tick all the boxes and provide a secure and complete system on top of giving a good user experience.
Modern access control is provided by smartphones and their associated mobile applications. In general, we can split up the discussion into two sections: the access control apps for mobile unlocks and using your smartphone as a key card.
Mobile Unlocks - Access Control Apps
For a more in-depth dive into mobile unlocks, please refer to this article. Apps will exist in Android and iPhone versions, and most of these apps will have an interface that you can use to view all the places and all the locks to which you have access.
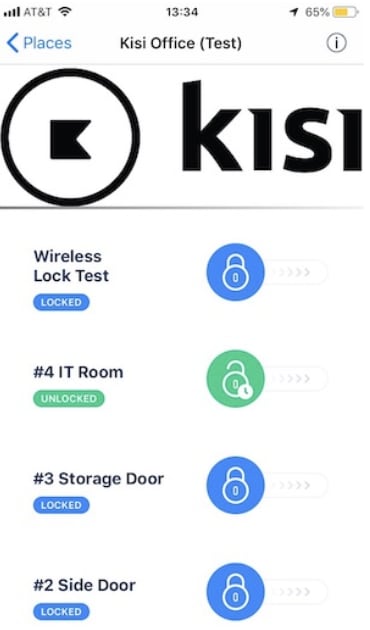
These mobile unlocks definitely fit the modularity criteria: a bunch of people can have access to the same lock, and all unlock it via their app. It also fits the customizability criteria: different people can have different access levels, and access to different sets of doors. An admin may be able to access all the doors from her app, whereas an employee might only have access to the front door of the office, for instance.
Your Smartphone As A Key Card
Another way that mobile phones manage access control is by using the NFC and Bluetooth chip in the phone as a direct alternative to a keycard. For more in-depth descriptions of this, please refer to our Bluetooth and our NFC articles!

Much like the mobile unlocks, these sorts of “tap to unlock” functionalities fulfill the modularity and customizability requirements, as the process of access granting is the exact same as that for mobile unlocks thanks to the power of the Bluetooth and NFC chips in smartphones!
Advantages of Using Smartphones for Access Control
Now that we know that mobile access control has all the versatility of older key and key card methods, we can look at its advantages: things that mobile access control does better than its alternatives.
Easy Onboarding/Offboarding
With mobile access control systems, you’ll generally have a web interface, and as an admin you can easily add and remove employees from access groups. No need to go around hassling people to give their keys back, or tracking them down to pass out keys or key cards. The process is seamless and smooth.
Employee tracking
Similarly, with a web interface, you can easily track data and track your employees’ access events. With a key, this is impossible, and with a key card, it’s complicated, as you need to keep track of who has what key. This information can easily become outdated as people share or lose track of their cards. But you can be certain they won’t trade phones for the day, so monitoring their movements becomes as easy as logging in.
Avoid Shared and Lost Credentials
As we mentioned before, keys and key cards are pretty easily shared, traded, or lost. This presents notable security issues, as an unwanted person could gain access to your space, and become a headache for any admin. However, by tying access control to peoples’ smartphones, you greatly reduce the risk of this happening.
Managing Cards from Mobile
Maybe Americans are too tied to their cards to ever give them up. Maybe the physical card will never go out of style because we like the idea of having some physical access token too much. In that case, maybe a compromise is in order.
With modern smartphone capabilities, and apps that leverage them, it’s actually possible to manage all your smart cards from your mobile device — and we don’t mean keeping a digital log of all your smart cards on a document. With the NFC Tools app on Android phones, you can read NFC card IDs and get all the relevant information you might want, and enroll the cards to work with various other apps based on that ID information.

With these sorts of tools, even if you don’t want to totally get rid of key cards, it’s easier than ever to manage them, keep track of them, and assign them the way you want to.
Closing Thoughts
Keys and key cards are great systems and have proved their mettle time and time again over the millennia. However, as the world is changing, so too must access control evolve. Thankfully, today there exist modern, future-proof alternatives to these methods, in the form of mobile access control. With all of these advantages and more, it’s easier than ever to avoid using key cards and old rusty keys.
Save time. Enhance security.
Modernize your access control with remote management and useful integrations.

